2015-Taxonomy (Networking)
The following list represents the latest pattern collection that was published 2014/2015 in [1], and improved by [2] and [3]. Additional minor updates were provided by [4-6]. Each pattern comprises a number (pattern ID), the authors and publication reference where the pattern was first published*, a brief illustration of the pattern’s use, a context (where can the pattern be found in the hierarchy of patterns) and a link to publications which provide evidence for the existence of the pattern.
Please note that this taxonomy was incorporated into the generic taxonomy (details are described in the paper that presents the generic taxonomy).
*Please note that the author of a pattern is not necessarily the inventor of a particular hiding technique. Instead he/she is the one who recognized the pattern within different hiding techniques. The authors of the particular hiding techniques are listed in the `Evidence’ attribute of each pattern.
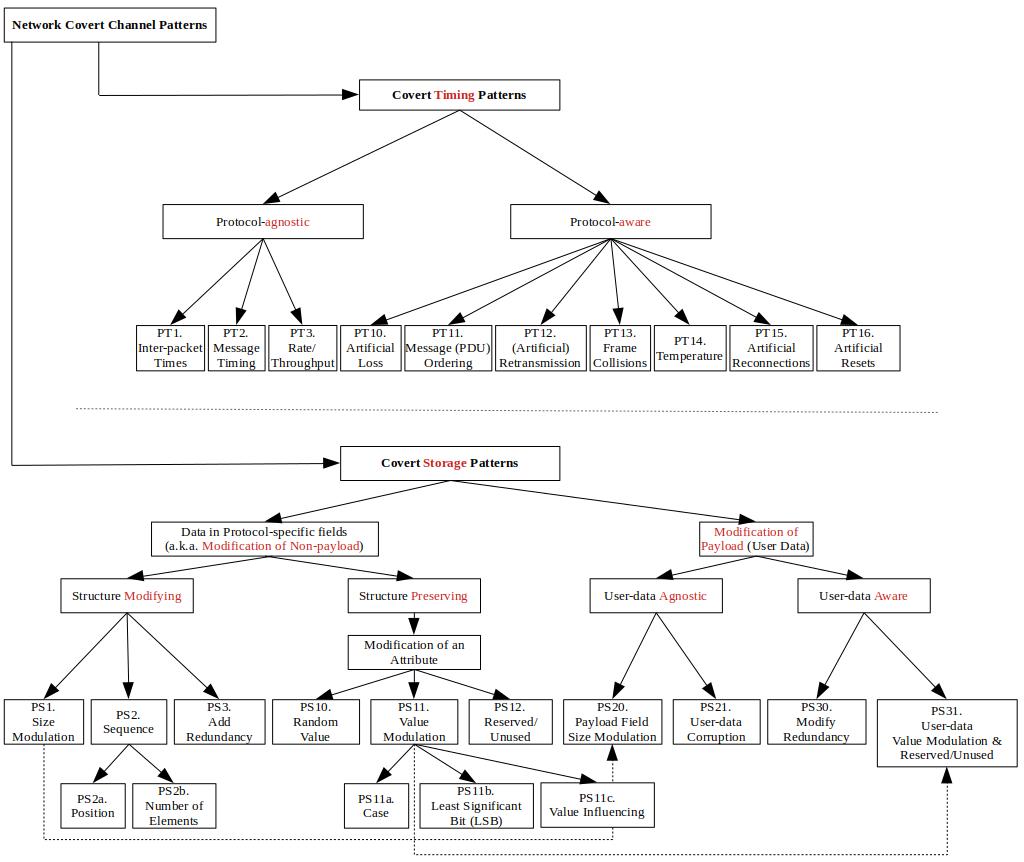 Latest Version of the Hiding Patterns Hierarchy (based on [1]; updated by [2-6]), version: Mar-25-2022.
Latest Version of the Hiding Patterns Hierarchy (based on [1]; updated by [2-6]), version: Mar-25-2022.
PT1. Inter-packet Times (also P8. Inter-arrival Time Pattern)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1], updated by [2]. Illustration The covert channel alters timing intervals between network PDUs (interarrival times) to encode hidden data. Context Network Covert Timing Channels -> Protocol-agnostic Evidence G. Shah, A. Molina, and M. Blaze. 2006. Keyboards and Covert Channels. In Proc. 15th USENIX Security Symposium. USENIX Association, 59–75.
C. G. Girling. 1987. Covert Channels in LAN’s. IEEE Transactions on Software Engineering 13 (February 1987), 292–296. Issue 2.
S. Cabuk. 2006. Network covert channels: Design, analysis, detection, and elimination. Ph.D. Dissertation. Purdue University
See [1] for additional evidence entries.Implementation Covert Channels Evaluation Framework (CCHEF) as well as 8 PT2. Message Sequence Timing
Initial publication W. Mazurczyk, S. Wendzel, S. Zander et al. in [2]. Illustration Hidden data is encoded in the timing of message sequences, e.g. acknowledging every n’th received packet or sending commands m times. Context Network Covert Timing Channels -> Protocol-agnostic Evidence see [2]. Implementation PT3. Rate/Throughput Pattern (also P9. Rate)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel sender alters the data rate of traffic from itself or a third party to the covert channel receiver. Alias Throughput Pattern Context Network Covert Timing Channels -> Protocol-agnostic Evidence X. Li, Y. Zhang, F.T. Chong, and B.Y. Zhao. 2011. “A Covert Channel Analysis of a Real Switch”. Technical Report. Dep. of Computer Science, University of California, Santa Barbara.
T. G. Handel and M. T. Sandford, II. 1996. Hiding Data in the OSI Network Model. In Proc. First International Workshop on Information Hiding. Springer, London, UK, 23–38.
Another possible example for a rate pattern-based hiding technique is mentioned in [1].Implementation ?
PT10. Artificial Message/Packet Loss Pattern (derived from original P4. PDU Corruption/Loss Pattern)
Initial publication W. Mazurczyk, S. Wendzel, S. Zander et al. in [2].
However, this pattern is based on the original P4. PDU Corruption/Loss Pattern, which was introduced by S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1]. The pattern P4 was split up into two separate patterns (the Frame Collisions pattern and Artificial Loss pattern). P4 was later also re-invented for user-data as PS21. User-data Corruption, cf. [3].Illustration The covert channel signals hidden information via artificial loss of transmitted messages (PDUs). Context Network Covert Timing Channels -> Protocol-aware Evidence see [2] Implementation PT11. Message Ordering Pattern (also P10 PDU Order Pattern)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] ** Alias(es)** PDU Order [1], Manipulated Message Ordering [2], Message Ordering [3]. Illustration The covert channel encodes data using a synthetic PDU order for a given number of PDUs flowing between covert sender and receiver. Context Network Covert Timing Channels -> Protocol-aware Evidence K. Ahsan and D. Kundur. 2002. Practical Data Hiding in TCP/IP. In Proc. Workshop on Multimedia Security at ACM Multimedia ’02.
X. Luo, E.W.W. Chan, and R.K.C. Chang. 2007. Cloak: A Ten-Fold Way for Reliable Covert Communications. In Proc. 12th European Symposium On Research In Computer Security (ESORICS 2007) (LNCS), Vol. 4734. Springer.
A. El-Atawy and E. Al-Shaer. 2009. Building Covert Channels over the Packet Reordering Phenomenon. In INFOCOM 2009. 2186–2194.
See [1] and [2] for more evidence entries.Implementation PT12. Re-Transmission Pattern (also P11)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration A covert channel re-transmits previously sent or received PDUs. Context Network Covert Timing Channels -> Protocol-aware Evidence C. Kraetzer, J. Dittmann, A. Lang, and T. Kuehne. 2006. WLAN Steganography: A First Practical Review. In Proc. 8th Workshop on Multimedia and Security (MMSEC’06). 17–22.
S. Zillien, S. Wendzel: Detection of Covert Channels in TCP Retransmissions, in Proc. NordSec 2018, Springer, 2018.
See [1] for two additional examples of such hiding techniques based on the re-transmission pattern.Implementation S. Zillien, S. Wendzel: Detection of Covert Channels in TCP Retransmissions, in Proc. NordSec 2018, Springer, 2018. PT13. Frame Collisions Pattern (derived from original P4. PDU Corruption/Loss Pattern)
Initial publication W. Mazurczyk, S. Wendzel, S. Zander et al. in [2].
However, this pattern is based on the original P4. PDU Corruption/Loss Pattern, which was introduced by S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1]. The pattern P4 was split up into two separate patterns (the Frame Collisions pattern and Artificial Loss pattern). P4 was later also re-invented for user-data as PS21. User-data Corruption, cf. [3].Illustration The sender causes artificial frame collisions to signal hidden information. Context Network Covert Timing Channels -> Protocol-aware Evidence see [2] Implementation PT14. Temperature Pattern
Initial publication W. Mazurczyk, S. Wendzel, S. Zander et al. in [2]. Illustration The sender influences a third-party node’s CPU temperature, e.g. using burst traffic. This influences the node’s clock skew. The clock skew can then be interpreted by the covert receiver by interacting with the node. Context Network Covert Timing Channels -> Protocol-aware Evidence see [2] Implementation PT15. Artificial Reconnections
Initial publication A. Mileva, A. Velinov, L. Hartmann et al. in [5]. Illustration The Artificial Reconnections Pattern employs artificial (forced) reconnections to transfer secret messages. The covert sender influences connection states of third-party nodes in a way that their connections to either a central element (e.g., an MQTT broker or a server) or a peer (in a peer-to-peer network) are terminated and then established again (i.e., a reconnect is performed). The covert receiver must be capable of monitoring these reconnects, e.g., either by compromising the central/peer element or in a passive network observer situation, like a MitM location. Encoding works by assigning secret values to third-party, so that a reconnect of a particular node represents the transfer of the secret symbol assigned to that node. Another scenario for this pattern can also be a chatroom or a gaming server with a large number of clients that reconnect automatically after being disconnected (source: [5]). Context Network Covert Timing Channels -> Protocol-aware Evidence see [5] and [7] Implementation PT16. Artificial Resets
Initial publication L. Hartmann, S. Zillien, S. Wendzel in [6]. Illustration The pattern PT16 Artificial Resets is embedded by a CS that causes a connection reset of third-party nodes, whose connection states are observed by one or more CRs. The pattern is a protocol-aware timing pattern.
So far, the pattern has only been described for an indirect covert channel.Context Network Covert Timing Channels -> Protocol-aware Evidence see [6] Implementation https://github.com/NIoSaT/CoAP-Covert-Channels features the first known implementation and is based on the IoT protocol CoAP.
PS1. Size Modulation Pattern (also P1)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel uses the size of a header element or a PDU to encode a hidden message. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Modifying Evidence C. G. Girling. 1987. Covert Channels in LAN’s. IEEE Transactions on Software Engineering 13 (February 1987), 292–296. Issue 2.
M. Wolf. 1989. Covert channels in LAN protocols. In Proc. Local Area Network Security. LNCS, Vol. 396. Springer, 89–101.
S. J. Murdoch and S. Lewis. 2005. Embedding Covert Channels into TCP/IP. In Proc. Information Hiding Conference 2005 (LNCS), Vol. 3727. Springer, 247–261.
Steffen Wendzel, Florian Link, Daniela Eller, Wojciech Mazurczyk: Detection of Size Modulation Covert Channels Using Countermeasure Variation, Journal of Universal Computer Science (J.UCS), Vol. 25(11), 2019.
For more evidence entries cf. [1].Implementation The implementation can be realized using CCEAP. An alternative is: C. Heinz: TLSCC (University of Hagen) Known Pattern-based Countermeasures Steffen Wendzel, Florian Link, Daniela Eller, Wojciech Mazurczyk: Detection of Size Modulation Covert Channels Using Countermeasure Variation, Journal of Universal Computer Science (J.UCS), Vol. 25(11), 2019. PS2. Sequence Pattern (also P2)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel alters the sequence of header/PDU elements to encode hidden information. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Modifying Evidence A. Dyatlov and S. Castro. 2005. Exploitation of data streams authorized by a network access control system for arbitrary data transfers: tunneling and covert channels over the HTTP protocol. Technical Report. Gray-World.net.
R. Rios, J.A. Onieva, and J. Lopez. 2012. HIDE DHCP: Covert Communications Through Network Configuration Messages. In Proc. IFIP TC 11 27th International Information Security Conference. Springer.
X.-g. Zou, Q. Li, S.-H. Sun, and X. Niu. 2005. The Research on Information Hiding Based on Command Sequence of FTP Protocol. In Proc. 9th Int. Conf. on Knowledge-Based Intelligent Information and Engineering Systems (KES 2005), Part III (LNCS), Vol. 3683. Springer Berlin Heidelberg, 1079–1085.Implementation ? PS2.a. Position Pattern (also P2a)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel alters the position of a given header/PDU element to encode hidden information. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Modifying -> Sequence Evidence R. Rios, J.A. Onieva, and J. Lopez. 2012. HIDE DHCP: Covert Communications Through Network Configuration Messages. In Proc. IFIP TC 11 27th International Information Security Conference. Springer.
For further examples cf. [1].Implementation ? PS2.b. Number of Elements Pattern (also P2b)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel encodes hidden information by the number of header/PDU elements transferred. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Modifying -> Sequence Evidence R. Rios, J.A. Onieva, and J. Lopez. 2012. HIDE DHCP: Covert Communications Through Network Configuration Messages. In Proc. IFIP TC 11 27th International Information Security Conference. Springer.
W. Mazurczyk and K. Szczypiorski. 2012. Evaluation of steganographic methods for oversized IP packets. Telecommunication Systems 49, 2 (2012), 207–217.
A third example is mentioned in [1].Implementation ? PS3. Add Redundancy Pattern (also P3)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel creates new space within a given header element or within a PDU to hide data into. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Modifying Evidence Z. Trabelsi and I. Jawhar. 2010. Covert File Transfer Protocol Based on The IP Record Route Option. Journal of Information Assurance and Security (JIAS) 5, 1 (2010).
T. Graf. 2003. Messaging over IPv6 Destination Options (2003). Retrieved: December 2013.
A. Getchell. 2008. RE: For those interested in covert channels. (2008). A posting on the securityfocus penetration testing mailinglist, retrieved: December 2013.
For further evidence entries cf. [1].Implementation CCEAP
This tool by Binni Shah adds additional option(s) to the TCP header to carry covert data (good explanation is available).
C. Heinz: TLSCC (University of Hagen)
PS10. Random Value Pattern (also P5)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel embeds hidden data in a header element containing a (pseudo-)random value. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Preserving -> Modification of an Attribute Evidence J. Keller, S. Wendzel. Reversible and Plausibly Deniable Covert Channels in One-Time Passwords Based on Hash Chains, Applied Sciences, Vol. 11(2), MDPI, 2021.
C. H. Rowland. 1997. Covert Channels in the TCP/IP Protocol Suite. First Monday 2, 5 (May 1997).
J. Rutkowska. 2004. The implementation of passive covert channels in the Linux kernel. (2004). Speech held at the 21st Chaos Communication Congress, Berlin, Germany
N. Lucena, J. Pease, P. Yadollahpour, and S. J. Chapin. 2004. Syntax and Semantics-Preserving Application Layer Protocol Steganography. In Proceedings of 6th Information Hiding Workshop.
In [1], additional information on the evidence is provided.Implementation e.g. C. Heinz: TLSCC (University of Hagen) PS11. Value Modulation Pattern (also P6)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel selects one of the n values that a header element can contain to encode a hidden message. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Preserving -> Modification of an Attribute Evidence T. Schmidbauer et al.: Introducing Dead Drops to Network Steganography using ARP-Caches and SNMP-Walks, in Proc. ARES 2019. This channel is an indirect variant of a Value Modulation as an ARP cache of a third party host stores the data (for quite some time).
C. G. Girling. 1987. Covert Channels in LAN’s. IEEE Transactions on Software Engineering 13 (February 1987), 292–296. Issue 2. S. Zander, G.J. Armitage, and P.A. Branch. 2006. Covert Channels in the IP time to live field. In Australian Telecommunication Networks and Applications Conference (ATNAC 2006). 298–302.
N. Lucena, G. Lewandowski, and S. Chapin. 2006. Covert Channels in IPv6. In Proc. 5th International Workshop on Privacy Enhancing Technologies (PET 2005). LNCS, Vol. 3856. Springer, 147–166.
See [1] for more evidence entries.Implementation Covert Channels Evaluation Framework (CCHEF)
CCEAPPS11.a. Case Pattern (previously known as P6a)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel uses case-modification of letters in header elements to encode hidden data. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Preserving -> Modification of an Attribute -> Value Modulation Evidence A. Dyatlov and S. Castro. 2005. Exploitation of data streams authorized by a network access control system for arbitrary data transfers: tunneling and covert channels over the HTTP protocol. Technical Report. Gray-World.net.
R. Patuck and J. Hernandez-Castro. 2013. Steganography using the Extensible Messaging and Presence Protocol (XMPP). CoRR abs/1310.0524 (2013).
[1] provides additional examples of possible case pattern-based techniques.Implementation ? PS11.b. Least Significant Bit (LSB) Pattern (previously known as P6b)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel uses the least significant bit(s) of header elements to encode hidden data. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Preserving -> Modification of an Attribute -> Value Modulation Evidence T. G. Handel and M. T. Sandford, II. 1996. Hiding Data in the OSI Network Model. In Proc. First International Workshop on Information Hiding. Springer, London, UK, 23–38.
J. Giffin, R. Greenstadt, P. Litwack, and R. Tibbetts. 2003. Covert messaging through TCP timestamps. In Proc. 2nd International Conference on Privacy Enhancing Technologies. Springer, 194–208.
R. Rios, J.A. Onieva, and J. Lopez. 2012. HIDE DHCP: Covert Communications Through Network Configuration Messages. In Proc. IFIP TC 11 27th International Information Security Conference. Springer.
More evidence entries are provided in [1].Implementation Covert Channels Evaluation Framework (CCHEF) PS11.c. Value Influencing Pattern
Initial publication A. Velinov, A. Mileva, S. Wendzel, W. Mazurczyk (2019) in [4] Illustration The covert channel sender (directly or indirectly) influences some (out of n possible) values in a way that a covert channel receiver can determine the value. In other words, the value is not directly written, but influence by altering another value or surrounding networking conditions. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Preserving -> Modification of an Attribute -> Value Modulation Evidence see [4] Implementation - PS12. Reserved/Unused Pattern (also P7)
Initial publication S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1] Illustration The covert channel encodes hidden data into a reserved or unused header/PDU element. Context Network Covert Storage Channels -> Modification of Non-Payload -> Structure Preserving -> Modification of an Attribute Evidence M. Wolf. 1989. Covert channels in LAN protocols. In Proc. Local Area Network Security. LNCS, Vol. 396.Springer, 89–101.
T. G. Handel and M. T. Sandford, II. 1996. Hiding Data in the OSI Network Model. In Proc. First International Workshop on Information Hiding. Springer, London, UK, 23–38.
K. Ahsan and D. Kundur. 2002. Practical Data Hiding in TCP/IP. In Proc. Workshop on Multimedia Security at ACM Multimedia ’02.
See [1] for additional evidence entries.Implementation ?
PS20. Payload Field Size Modulation (derived from PS1)
Initial publication W. Mazurczyk, S. Wendzel, K. Cabaj in [3].
However, this pattern is based on the original PS1. Size Modulation Pattern, which was introduced by S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1].Illustration This pattern uses a size of the payload field of a flow’s PDUs/messages to encode the hidden message. This pattern is a variant (child) of the pattern P1. Size Modulation of [1] which has been already defined for the modification of the non-payload branch of storage methods. Context Network Covert Channel Patterns -> Covert Storage Channel Patterns -> Modification of Payload -> User-data Agnostic Evidence Modulate the size of the data block field in Ethernet frames, cf. Girling’87.
Any other method that modulates the size of the payload field in any network protocol.Implementation PS21. User-data Corruption (derived from original P4. PDU Corruption/Loss Pattern)
Initial publication W. Mazurczyk, S. Wendzel, K. Cabaj in [3].
However, this pattern is based on the original P4. PDU Corruption/Loss Pattern, which was introduced by S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1]. The pattern P4 was split up into two separate patterns (the Frame Collisions pattern and Artificial Loss pattern), cf. [2]. P4 was later also re-introduced for user-data as PS21. User-data Corruption, cf. [3].Illustration This pattern is related to the cases when steganographic methods do not take into account what kind of user-data is carried within a payload field and/or what its characteristic is (blind modification). It can be applied to single PDUs or to multiple PDUs (a flow). This typically happens if parts of (or the whole) user-data is replaced with secret bits and thus the user-data is corrupted/lost. Context Network Covert Channel Patterns -> Covert Storage Channel Patterns -> Modification of Payload -> User-data Agnostic Evidence see [3]. Implementation
PS30. Modify Redundany
Initial publication W. Mazurczyk, S. Wendzel, K. Cabaj in [3]. Illustration This pattern is used when it is possible to exploit the redundancy of the user-data by means of transforming them in such a way that a free space for secret data is obtained (e.g. by means of transcoding). This pattern is a bit similar to the pattern Add Redundancy defined in [1] but can also decrease redundancy and is applied to payload instead of meta-data. Context Network Covert Channel Patterns -> Covert Storage Channel Patterns -> Modification of Payload -> User-data Aware Evidence See [3] for references. At least the following ideas were published that belong to this pattern:
1. Compress existing user-data in order to make a space for secret data.
2. Transform the VAD-enabled IP telephony voice stream into non-VAD one and fill the gaps using artificially generated RTP packets containing secret data.
3. Approximate the F0 parameter of the Speex codec which carries information about the pitch of the speech signal and use the ``saved’’ space for secret data.Implementation PS31. User-data Value Modulation and Reserved/Unused
Initial publication W. Mazurczyk, S. Wendzel, K. Cabaj in [3].
However, this pattern is based on the original PS11 Value Modulation and PS12 Rserved/Unused Patterns, which were introduced by S. Wendzel, S. Zander, B. Fechner, C. Herdin in [1].Illustration Characteristic features of user-data can be utilized to store secret information. This includes applying methods like LSB modification to speech samples or digital images carried within the payload field. Compared with previous patterns this is a targeted modification. This pattern is analogous to the combination of the patterns. Context Network Covert Channel Patterns -> Covert Storage Channel Patterns -> Modification of Payload -> User-data Aware Evidence See [3] for references. At least the following ideas were published that belong to this pattern:
1. Encode a stream of information by spreading the encoded data across as much of the frequency spectrum as feasible (e.g. DSSS).
2. Embeds secret data into a carrier audio signal by introducing an echo (a.k.a. echo hiding).
3. Replacing the least significant bit of e.g. each voice sample with secret data (LSB).Implementation
Video Introduction to Patterns: https://www.youtube.com/watch?v=0ztPHur0LUY
Implementation: Most of these patterns, excluding the payload-specific patterns, can be created with the CCEAP tool.
Bibliography:
[1] S. Wendzel, S. Zander, B. Fechner, C. Herdin: Pattern-based Survey and Categorization of Network Covert Channel Techniques, ACM Computing Surveys, Vol. 47, Issue 3, pp. 50:1-26, ACM, 2015. An early version of the article is available here
[2] W. Mazurczyk, S. Wendzel, S. Zander, A. Houmansadr, K. Szczypiorski: Information Hiding in Communication Networks, Wiley, 2016. Chapters 3 and 8 contain discussions on hiding patterns, basically on the basis of [1] but with an extension of timing-based patterns.
[3] W. Mazurczyk, S. Wendzel, K. Cabaj: Towards Deriving Insights into Data Hiding Methods Using Pattern-based Approach, in Proc. Second International Workshop on Criminal Use of Information Hiding (CUING 2018) at ARES, pp. 10:1-10:10, ACM, 2018.
[4] A. Velinov, A. Mileva, S. Wendzel, W. Mazurczyk: Covert Channels in MQTT-based Internet of Things, IEEE ACCESS, Vol. 7, pp. 161899-161915, 2019.
[5] A. Mileva, A. Velinov, L. Hartmann, S. Wendzel, W. Mazurczyk: Comprehensive Analysis of MQTT 5.0 Susceptibility to Network Covert Channels, Computers & Security, Elsevier, 2021.
[6] L. Hartmann, S. Zillien, S. Wendzel: Reset- and Reconnection-based Covert Channels in CoAP. In: Proc. European Interdisciplinary Cybersecurity Conference (EICC), 2021.
[7] Sebastian Zillien, Steffen Wendzel: Reconnection-based Covert Channels in Wireless Networks. In: Proc. 36th IFIP TC-11 International Information Security and Privacy Conference (IFIP SEC 2021). Springer, 2021.
[8] Sebastian Zillien, Steffen Wendzel: Weaknesses of popular and recent covert channel detection methods and a remedy. In: IEEE Trans. Dep. Sec. Comp. (TDSC), in press.