2021-Taxonomy
This is the obsolete 2021 version of the pattern collection which was updated in 2022 (cf. Pattern Collection v2).
If you prefer using this taxonomy, its presentation and glossary can be found here: Presentation and Glossary. However, please note that the 2022-version fixes several issues of the 2021-version.
The original publication describing the 2021-taxonomy version is: Wendzel S, Caviglione L, Mazurczyk W, Mileva A, Dittmann J, Krätzer C, Lamshöft K, Vielhauer C, Hartmann L, Keller J, Neubert T (2021): A Revised Taxonomy of Steganography Embedding Patterns. In: Proc. 16th International Conference on Availability, Reliability and Security (ARES 2021). ACM, DOI: 10.1145/3465481.3470069.
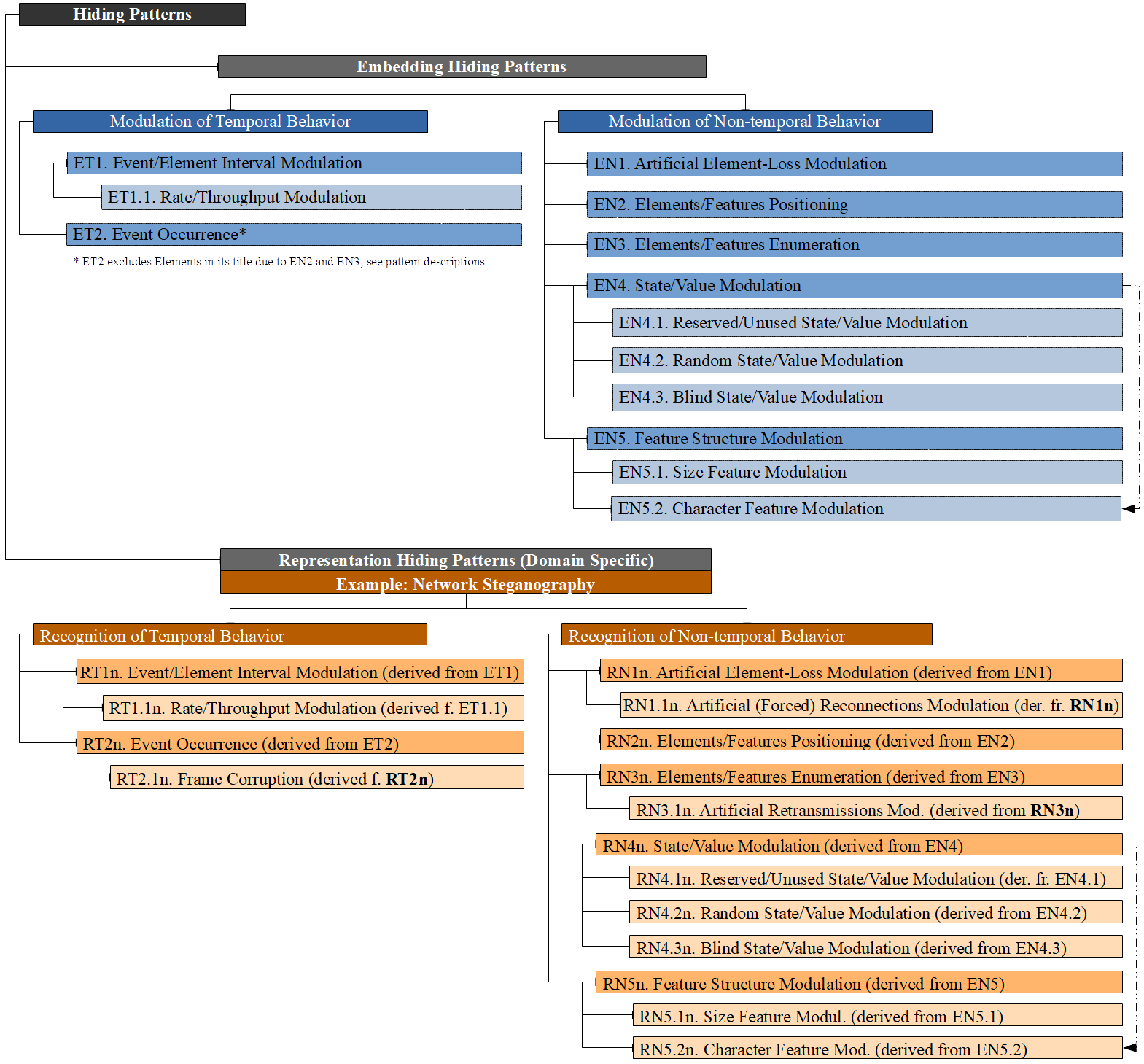
Embedding Hiding Patterns
Modulation of Temporal Behavior:
ET1. Event/Element Interval Modulation
ET1.1. Rate/Throughput Modulation
ET2. Event Occurrence
Modulation of Non-temporal Behavior:
EN1. Artificial Element-Loss
EN2. Elements/Features Positioning
EN3. Elements/Features Enumeration
EN4. State/Value Modulation
EN4.1. Reserved/Unused State/Value Modulation
EN4.2. Random State/Value Modulation
EN4.3. Blind State/Value Modulation
EN5. Feature Structure Modulation
EN5.1. Size Feature Modulation
EN5.2. Character Feature Modulation
Representation Hiding Patterns (Domain Specific) Example: Network Steganography
Recognition of Temporal Behavior:
RT1n. Event/Element Interval Modulation (derived from ET1)
RT1.1n. Rate/Throughput Modulation (derived from ET1.1)
RT2n. Event Occurrence (derived from ET2)
RT2.1n. Frame Corruption (derived from RT2n)
Recognition of Non-temporal Behavior:
RN1n. Artificial Element-Loss (derived from EN1)
RN1.1n. Artificial (Forced) Reconnections Modulation (derived from RN1n)
RN2n. Elements/Features Positioning (derived from EN2)
RN3n. Elements/Features Enumeration (derived from EN3)
RN3.1n. Artificial Retransmissions Modulation (derived from RN3n)
RN4n. State/Value Modulation (derived from EN4)
RN4.1n. Reserved/Unused State/Value Modulation (derived from EN4.1)
RN4.2n. Random State/Value Modulation (derived from EN4.2)
RN4.3n. Blind State/Value Modulation (derived from EN4.3)
RN5n. Feature Structure Modulation (derived from EN5)
RN5.1n. Size Feature Modulation (derived from EN5.1)
RN5.2n. Character Feature Modulation (derived from EN5.2)
ET1. Event/Element Interval Modulation
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Inter-packet Times pattern from Wendzel et al., 2015. |
| Illustration | The covert message is embedded by modulating the gaps between succeeding events/elements. |
| Context | Embedding Hiding Patterns -> Modulation of Temporal Behavior |
| Evidence | 1) modulating the inter-packet gap between succeeding network packets (elements) or between connection establishments (events); 2) modulating the time-gap between succeeding cyber-physical actions, such as acoustic beeps. |
| Implementation |
ET1.1. Rate/Throughput Modulation
| Initial publication | Wendzel et al., 2015; however, meaning of the pattern was generalized in Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns to render it independent from the networking context |
| Illustration | The covert message is embedded by alternating the rate of events/elements (by introducing delays or by decreasing delays). Here, several inter-event/element intervals have to be modified in a row to embed a secret message, i.e., the message is not embedded into particular inter-event/element timings but in the overall rate/throughput. |
| Context | Embedding Hiding Patterns -> Modulation of Temporal Behavior |
| Evidence | 1) modulating the packet rate while sending traffic to some destination (by decreasing/increasing delays between send() actions); 2) modulating the number of produced items per hour in a production facility. |
| Implementation |
ET2. Event Occurrence
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Message Sequence Timing pattern from Mazurczyk et al., 2016. |
| Illustration | The covert message is encoded in the temporal location of events (in comparison to ET1.1, the rate of events is not directly modulated but events are triggered at specific moments in time, moreover, ET2 can be a single event while ET1.1 needs a sequence of elements). |
| Context | Embedding Hiding Patterns -> Modulation of Temporal Behavior |
| Evidence | 1) sending a specific packet at 6pm; 2) influencing the time at which a drone starts its journey to some destination (or its arrival time). |
| Implementation |
References:
Wojciech Mazurczyk, Steffen Wendzel, Sebastian Zander, Amir Houmansadr, and Krzysztof Szczypiorski: Information Hiding in Communication Networks: Fundamentals, Mechanisms, and Applications, IEEE Series on Information and Communication Networks Security, Wiley, 2016.
EN1. Artificial Element-Loss
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Artificial Loss pattern from Wendzel et al., 2015. |
| Illustration | The covert message is embedded by modulating the artificial loss of elements. |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) dropping TCP segments with an even sequence number; 2) removing commas in sentences Bender1996. |
| Implementation |
References:
Walter Bender, Daniel Gruhl, Norishige Morimoto, and Anthony Lu: Techniques for data hiding, IBM Systems Journal, 35 (Nos 3&4), IBM, pages 313–336, 1996.
EN2. Elements/Features Positioning
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns |
| Illustration | The covert message is embedded by modulating the position of a predefined (set of) element(s)/feature(s) in a sequence of elements/features. |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) position of an IPv4 option in the list of options; 2) placing a drink on a table to signal a Go player to play more defensive; 3) placing a specific character in a paragraph. |
| Implementation |
EN3. Elements/Features Enumeration
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns |
| Illustration | The covert message is embedded by altering the overall number of appearances of elements/features in a sequence. |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) fragmenting a network packet into either n or m (n ≠ m) fragments; 2) modulating the number of people wearing a t-shirt in a specific color in an image file; 3) repeating an element/feature by duplicating a white space character (or not) in a text Bender1996. |
| Implementation |
References:
Walter Bender, Daniel Gruhl, Norishige Morimoto, and Anthony Lu: Techniques for data hiding, IBM Systems Journal, 35 (Nos 3&4), IBM, pages 313–336, 1996.
EN4. State/Value Modulation
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Value Modulation pattern from Wendzel et al., 2015. |
| Illustration | The covert message is embedded by modulating the states or values of features. |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) performing intense computation to influence some temperature/clock-skew NIHbook; 2) modulating other physical states, such as proximity, visibility, force, height, acceleration, speed, etc. of certain devices; 3) changing values of the network packet header fields (e.g., target IP address of ARP Ji2010, Hop Count value in IPv6 Lucena2005 or the LSB in the IPv4 TTL); 4) modulate the x-y-z coordinates of a player in a 3D multiplayer online game Zander2008. |
| Implementation |
References:
Wojciech Mazurczyk, Steffen Wendzel, Sebastian Zander, Amir Houmansadr, and Krzysztof Szczypiorski: Information Hiding in Communication Networks: Fundamentals, Mechanisms, and Applications, IEEE Series on Information and Communication Networks Security, Wiley, 2016.
Liping Ji, Yu Fan, and Chuan Ma: Covert channel for local area network, 2010 IEEE International Conference on Wireless Communications, Networking and Information Security, pages 316-319, 2010.
Norka B. Lucena, Grzegorz Lewandowski, and Steve J. Chapin: Covert channels in IPv6, International Workshop on Privacy Enhancing Technologies, Springer, pages 147-166. 2005.
Sebastian Zander, Grenville Armitage, and Philip Branch: Covert channels in multiplayer first person shooter online games, 2008 33rd IEEE Conference on Local Computer Networks (LCN), IEEE, pages 215-222, 2008.
EN4.1. Reserved/Unused State/Value Modulation
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Reserved/Unused pattern from Wendzel et al., 2015. |
| Illustration | The covert message is embedded by modulating reserved/unused states/values. |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) overwriting the IPv4 reserved field HandelSandford96; 2) modulation of unused registers in embedded CPS equipment IoTStego17. |
| Implementation |
References:
Theodore G. Handel, and Maxwell T. Sandford II.: Hiding data in the OSI network model, Proceedings of the 1st International Workshop on Information Hiding, pages 23-38, 1996.
Steffen Wendzel, Wojciech Mazurczyk and Georg Haas: Don’t You Touch My Nuts: Information Hiding in Cyber Physical Systems, 2017 IEEE Security and Privacy Workshops (SPW), IEEE, pages 29-34, 2017.
EN4.2. Random State/Value Modulation
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Random (Value) Modulation pattern from Wendzel et al., 2015. |
| Illustration | A (pseudo-)random value or (pseudo-)random state is replaced with a secret message (that is also following a pseudo-random appearance) |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) replacing the pseudo-random content of a network header field with encrypted covert content; 2) encoding a secret message in the randomized selection of a starting player in an online chess game. |
| Implementation |
EN4.3. Blind State/Value Modulation
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns |
| Illustration | Blind corruption of data. |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) blindly overwriting a checksum of a PDU to corrupt a packet (or not) to embed hidden information; 2) blindly overwriting content of a file in a filesystem, neglecting its file header; 3) blindly overwriting a TCP payload. |
| Implementation |
EN5. Feature Structure Modulation
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns |
| Illustration | This hiding pattern comprises all hiding techniques that modulate the structural properties of a feature (but not states/values (EN4), positions (EN2) or number of appearances (EN3)). |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) increasing/decreasing the size of succeeding network packets; 2) changing the color/style of characters in texts. |
| Implementation |
EN5.1. Size Feature Modulation
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Size Modulation pattern from Wendzel et al., 2015. |
| Illustration | The covert message is embedded by modulating the size of an element. |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) create additional (unused) space in network packets for embedding hidden data, such as adding an ``unused’’ IPv6 destination option IPv6DestOptCC; 2) alternate the size of PNG files. |
| Implementation |
References:
Thomas Graf: Messaging over IPv6 Destination Options, Swiss Unix User Group, 2003.
EN5.2. Character Feature Modulation
| Initial publication | Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns |
| Illustration | Modulation of different features in characters, such as color, size (scale), font, position or size of different parts in some letters. Relations: Utilizes partially the same methods as EN4. State/Value Modulation (e.g., a HTTP header field’s character is also a value). Thus, both are linked in the Taxonomy. |
| Context | Embedding Hiding Patterns -> Modulation of Non-temporal Behavior |
| Evidence | 1) using upper/lower case letters in HTTP or SMTP requests Dyatlov2003; 2) modulating the color of characters in text steganography. |
| Implementation |
References:
Alex Dyatlov, and Simon Castro: Exploitation of Data Streams Authorized by a Network Access Control System for Arbitrary Data Transfers: Tunneling and Covert Channels over the HTTP Protocol, Gray-world, 2003.
Representation Patterns for Network Steganography
RT1n. Event/Element Interval Modulation
(derived from ET1)
RT1.1n. Rate/Throughput Modulation
(derived from ET1.1)
RT2n. Event Occurrence
(derived from ET2)
RT2.1n. Frame Corruption
(derived from RT2n)
- Original description (ih-patterns)
- Introduced by Wendzel et al., 2015
- Short Illustration: The sender causes artificial frame collisions to signal hidden information.
RN1n. Artificial Element-Loss
(derived from EN1)
RN1.1n. Artificial (Forced) Reconnections Modulation
(derived from RN1n)
- Original description (ih-patterns)
- Introduced by A. Mileva, A. Velinov, L. Hartmann et al.: Comprehensive Analysis of MQTT 5.0 Susceptibility to Network Covert Channels, Computers & Security, Elsevier, 2021.
- Short Illustration: The Artificial Reconnections Pattern employs artificial (forced) reconnections to transfer secret messages. The covert sender influences connections of third-party nodes in a way that their connections to either a central element (e.g., an MQTT broker or a server) or a peer (in a peer-to-peer network) are terminated and then established again (i.e., a reconnect is performed). The covert receiver must be capable of monitoring these reconnects, e.g., either by compromising the central/peer element or in a passive network observer situation, like a MitM location. Encoding works by assigning secret values to third-party, so that a reconnect of a particular node represents the transfer of the secret symbol assigned to that node. Another scenario for this pattern can also be a chatroom or a gaming server with a large number of clients that reconnect automatically after being disconnected.
RN2n. Elements/Features Positioning
(derived from EN2)
RN3n. Elements/Features Enumeration
(derived from EN3)
RN3.1n. Artificial Retransmissions Modulation
(derived from RN3n)
RN4n. State/Value Modulation
(derived from EN4)
RN4.1n. Reserved/Unused State/Value Modulation
(derived from EN4.1)
RN4.2n. Random State/Value Modulation
(derived from EN4.2)
RN4.3n. Blind State/Value Modulation
(derived from EN4.3)
RN5n. Feature Structure Modulation
(derived from EN5)
N5.1n. Size Feature Modulation
(derived from EN5.1)
RRN5.2n. Character Feature Modulation
(derived from EN5.2)
Bibliography:
Steffen Wendzel, Sebastian Zander, Bernhard Fechner, and Christian Herdin: Pattern-based Survey and Categorization of Network Covert Channels, ACM Comp. Surv., 2015.
Walter Bender, Daniel Gruhl, Norishige Morimoto, and Anthony Lu: Techniques for data hiding, IBM Systems Journal, 35 (Nos 3&4), IBM, pages 313–336, 1966.
Liping Ji, Yu Fan, and Chuan Ma: Covert channel for local area network, 2010 IEEE International Conference on Wireless Communications, Networking and Information Security, pages 316-319, 2010.
Norka B. Lucena, Grzegorz Lewandowski, and Steve J. Chapin: Covert channels in IPv6 International Workshop on Privacy Enhancing Technologies, Springer, pages 147-166. 2005.
Sebastian Zander, Grenville Armitage, and Philip Branch: Covert channels in multiplayer first person shooter online games, 2008 33rd IEEE Conference on Local Computer Networks (LCN), IEEE, pages 215-222, 2008.
Wojciech Mazurczyk, Steffen Wendzel, Sebastian Zander, Amir Houmansadr, and Krzysztof Szczypiorski: Information Hiding in Communication Networks: Fundamentals, Mechanisms, and Applications, IEEE Series on Information and Communication Networks Security, Wiley, 2016.
Theodore G. Handel, and Maxwell T. Sandford II.: Hiding data in the OSI network model, Proceedings of the 1st International Workshop on Information Hiding, pages 23-38, 1996.
Steffen Wendzel, Wojciech Mazurczyk and Georg Haas: Don’t You Touch My Nuts: Information Hiding in Cyber Physical Systems, 2017 IEEE Security and Privacy Workshops (SPW), IEEE, pages 29-34, 2017.
Thomas Graf: Messaging over IPv6 Destination Options, Swiss Unix User Group, 2003.
Alex Dyatlov, and Simon Castro: Exploitation of Data Streams Authorized by a Network Access Control System for Arbitrary Data Transfers: Tunneling and Covert Channels over the HTTP Protocol, Gray-world, 2003.
Presentation
Have a look at our video presentation:

Glossary
As a preliminary, we introduce some basic terminology, which will be used in the remainder of the paper. Even if the creation of a non- ambiguous vocabulary for steganographic applications is outside the scope of this work, reducing possible confusions or overloading of terms is fundamental to not void the efficiency and expressiveness of the taxonomy. Specifically, the term modifiable object we define as the general object type that will be used to contain the secret information. The process of hiding data within the cover depends on the used mechanism or pattern. In the following, we refer to such a process as embedding, injecting or hiding. The term modulating will be used in case of ambiguities, especially to highlight that the secret information is not directly stored but encoded by means of variations of the cover object. The amount of data that can be hidden will be denoted as the capacity. In general, patterns can be used both to describe the process of hiding information for storage purposes as well as to secretly move data among two endpoints. To avoid burdening the text, when the “transmissional” nature of the embedding process is not obvious, we will explicitly identify the covert sender and receiving side as to emphasize the origin and the destination of the steganographic communication. For the specific case of defining the taxonomy as well as to describe patterns, the following formal definitions have been introduced:
| Modifiable Objects | ||
|---|---|---|
| Event | a (timed or forced) appearance, which can be composed of several elements | 1) the appearance of a predefined character sequence; 2) a predefined specific sound in a video; 3) network connection establishment, reset or disconnection. |
| Element | represents a single unit of a whole sequence | 1) a word/character of a text; 2) a pixel of an image; 3) a network packet of the whole flow. |
| Feature | characterizes a property of an element to be modulated | 1) the color of a character; 2) the attribute of a tag in vector graphics; 3) the field / the size of a network packet. |
| Interval | specifies the temporal gap between two events | 1) the duration of an audio file; 2) the time between sending a message and receiving the related acknowledgement. |
| State/Value | denotes a non-temporal numerical or positional quantity of an element, feature, or event |
1) the values of TCP header fields (feature value); 2) the x-y-z coordinates of a player in a 3D game. |