Latest Patterns Taxonomy
Cite this page as follows (content was extracted from that paper):
- S. Wendzel, L. Caviglione, W. Mazurczyk, A. Mileva, J. Dittmann, C. Krätzer, K. Lamshöft, C. Vielhauer, L. Hartmann, J. Keller, T. Neubert, S. Zillien (2022): A Generic Taxonomy for Steganography Methods, pre-print, 2022.
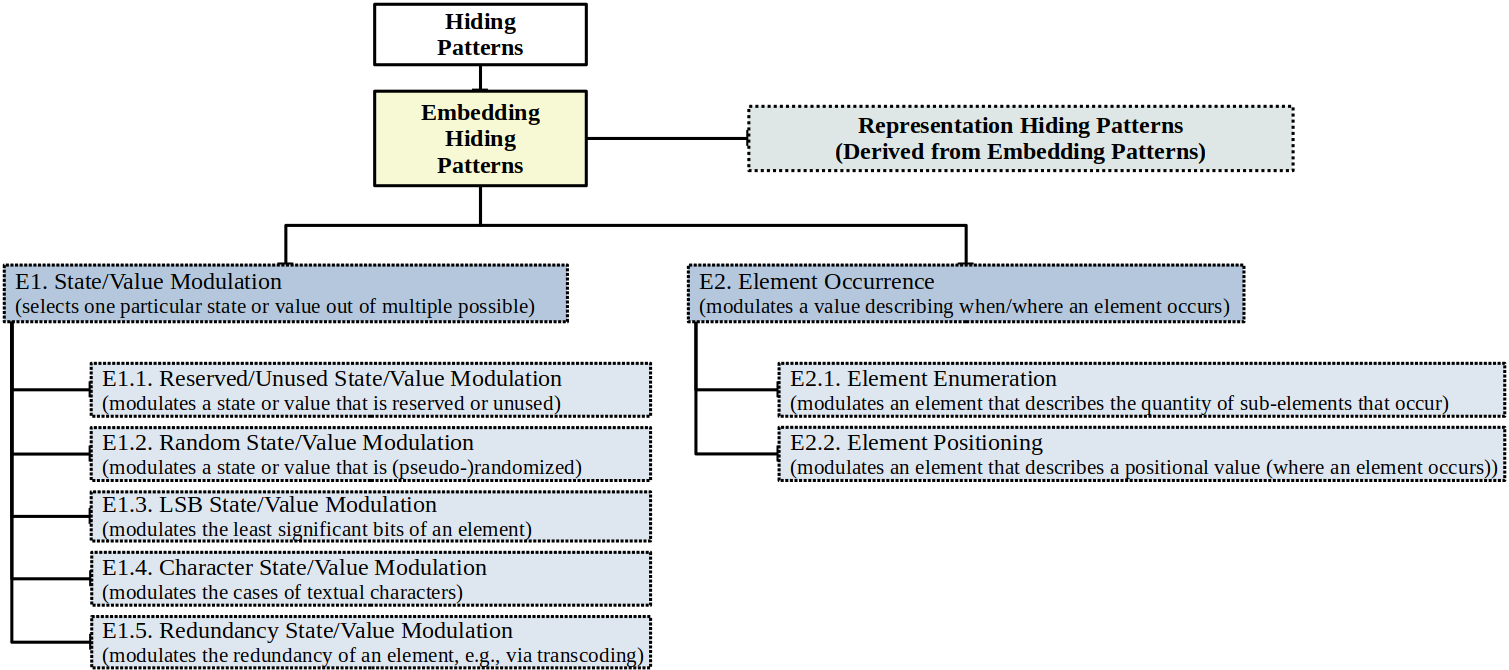
On this page, we first summarize the generic taxonomy. Afterwards, we explain the sub-taxonomys. Additional details can be found in the paper.
| Domain | Pattern | Sub-Pattern |
| General | EX | EXn1 |
| Network | EXn1 | EX.Xn1 |
| Text | EXt1 | EX.Xt1 |
| Digital Media | EXd1 | EX.Xd1 |
| CPS | EXc1 | EX.Xc1 |
| Filesystem | EXf1 | EX.Xf1 |
| Domain | Pattern | Sub-Pattern |
| General | RX | RXn1 |
| Network | RXn1 | RX.Xn1 |
| Text | RXt1 | RX.Xt1 |
| Digital Media | RXd1 | RX.Xd1 |
| CPS | RXc1 | RX.Xc1 |
| Filesystem | RXf1 | RX.Xf1 |
E1n1. Network State/Value Modulation
Initial publication Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Value Modulation pattern from Wendzel et al., 2015. Illustration The covert message is embedded by modulating the state or value of a network element, such as a frame, packet, header element, payload field etc. Original network steganography patterns PS11. Value Modulation (including all sub-patterns) and PS31. User-data Value Modulation, and partially: PT11. Message Ordering (only the aspect of modulating sequence numbers) and PT15. Artificial Reconnections/PT16. Artificial Resets (in both cases, some header fields, such as RST flags, must be modulated). Additionally: multiple patterns to cover E1n1’s sub-patterns (see particular descriptions below). Examples 1) Changing values of the network packet header fields (e.g., target IP address of ARP Ji et al., 2010) or the
2) Hop Count value in IPv6 Lucena et al., 2005 or the LSB in the IPv4 TTL.Implementation E1.1n1. Network Reserved/Unused State/Value Modulation
Initial publication Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Reserved/Unused pattern from Wendzel et al., 2015. Illustration The covert message is embedded by modulating reserved/unused states/values of network elements. Original network steganography patterns PS12. Reserved/Unused and, parts of PS3. Redundancy, parts of PS30. Modify Redundancy, as well as parts of PS31. User-data Value Modulation and Reserved/Unused. Examples 1) Ten examples for the original Reserved/Unused pattern are surveyed in Wendzel et al., 2015, showing that unused/reserved fields in IEEE 802.3 and 802.5 Handel et al., 1996, Wolf, 1989, Jankowski et al., 2010, IPv4 Handel et al., 1996, IP-IP, IPv6 Lucena et al., 2005, TCP Handel et al., 1996, Sadeghi et al., 2012, ICMP Stødle, 2009, daemon9, 1997, BACnet Wendzel et al., 2012, DHCP Rios et al., 2012, and IPSec Sadeghi et al., 2012 can be exploited by overwriting certain header fields, such as the IP Identifier. Moreover, additional and recent works have shown that more protocols are vulnerable due to their unused/reserved fields, such as
2) MQTT Velinov et al., 2019 and
3) SIP Mazurczyk and Szczypiorski, 2008.Implementation E1.2n1. Network Random State/Value Modulation
Initial publication Wendzel et al., 2021, A Revised Taxonomy of Steganography Embedding Patterns; generalized version of the Random (Value) Modulation pattern from Wendzel et al., 2015. Illustration A (pseudo-)random value or state of/in the network data is replaced with a secret message (that is also following a pseudo-random appearance). Original network steganography patterns PS10. Random Value and PS33. User-data Random Value Modulation. Examples 1) Wendzel et al., 2015 already mentions some examples, such as the utilization of the pseudo-random IP Identifier field Rowland, 1997, the TCP ISN Rowland, 1997, Rutkowska, 2004, the DHCP xid field Rios et al., 2012 and the SSH MAC field Lucena et al., 2004. Additional examples can be found in
2) Cryptographic protocols that use nonces during the challenge-response process Schmidbauer et al., 2022 as well as in
3) IoT protocols with random value fields, such as MQTT Velinov et al., 2019.Implementation E1.3n1. Network LSB State/Value Modulation
Initial publication Illustration The LSB of network elements are modulated. Original network steganography patterns PS11.b. LSB Modulation. Examples 1) Wendzel et al., 2015 provides several examples, such as the modulation of the LSBs in the IPv6 Hop Limit field Lucena et al., 2005, IPv4 TTL field, modulation of the IP timestamp option’s LSB Handel et al., 1996, TCP timestamp option Giffin et al., 2003, DHCP’s LSB of the secs field Rios et al., 2012, the BACnet hop count field, or the XMPP id attributes LSB Patuck and Hernandez-Castro, 2013.
2) Recent work has applied the LSB method to the Modbus protocol Bernieri et al., 2020.Implementation E1.4n1. Network Character State/Value Modulation
Initial publication Illustration The features of characters in network elements are modulated. Original network steganography patterns PS11.a. Case Modulation. Examples Case modulation of characters in HTTP headers Dyatlov and Castro, 2005. This method can also be applied to several other textual protocols, such as SMTP, IMAP, POP3, NNTP etc. Implementation E1.5n1. Network Redundancy State/Value Modulation
Initial publication Illustration The redundancy of a network element’s content is modulated (this is usually applied by a succeeding pattern that fills the gained space with covert data), e.g., by means of compression. Original network steganography patterns Part of PS30. Modify Redundancy. Examples Three examples of Mazurczyk et al., 2018 can be adjusted in their formulation to reflect this pattern:
1) Compression of existing payload (gained space can be used by E1.1n1. Reserved/Unused State/Value Modulation afterwards) Mazurczyk et al., 2014
2) Transformation of the VAD-enabled IP telephony voice stream into a non-VAD one and fill the gaps using artificially generated RTP packets containing secret data by applying another pattern Schmidt et al., 2017
3) Approximation of the F0 parameter of the Speex codec which carries information about the pitch of the speech signal (again, the saved space can then be used by another pattern) Jankowski et al., 2013.Implementation E2n1. Network Element Occurrence
Initial publication Illustration The covert message is encoded in the spatial or temporal location of network elements, which can also, e.g., influence the rate or overall number of packets appearing in a flow (succeeding messages occur shortly or long after previous ones). Original network steganography patterns PT10. Artificial Loss and PT12. Retransmission as well as multiple patterns to cover E2n1’s sub-patterns (see particular descriptions below). Examples 1) Sending a specific frame or packet multiple times (retransmission) as done in case of IEEE 802.11 Kraetzer et al., 2006 or TCP Zillien and Wendzel, 2018
2) Performing a high number of frame transmissions (e.g., so that their occurrences influence the rate/throughput of a network link Li et al., 2011)
3) Selecting one out of multiple possible IPv4 option headers to appear
4) Dropping TCP segments with an even sequence number (artificial loss, i.e., non-occurrence or occurrence of all other elements of a flow, except the dropped ones) or
5) Not acknowledging TCP packets Mazurczyk et al., 2011 (again a form of non-occurrence).Implementation E2.1n1. Network Element Enumeration
Initial publication Illustration An attribute describing the quantity of network sub-elements is modulated. This pattern also applies if sub-elements are added to a network element to increase its overall size (e.g., by adding more sub-elements to the payload in network packets). Original network steganography patterns PT2. Message Sequence Timing, PT12. Retransmission, PS1. Size Modulation, PS2.b. Number of Elements, PS20. Payload Field Size Modulation, as well as parts of PS3. Add Redundancy and PS32. User-data Sequence Modulation. Examples 1) Fragmenting a network packet into either n or m (n≠m) fragments Mazurczyk and Szczypiorski, 2012
2) Letting network packets or commands occur just once or multiple times (e.g., artificial TCP segment or FTP command re-transmissions) Zillien and Wendzel, 2018, Zou et al., 2005
3) Encoding secret information through the number of IPv6 extension headers or IPv4 option headers
4) Creating additional (unused) space in network packets, such as adding an “unused” IPv6 destination option Graf, 2003 (a variant of the former PS1. Size Modulation) or integration of additional SMTP header lines Getchell, 2008
5) Modulating the number of DHCP options Rios et al., 2012.Implementation E2.2n1. Network Element Positioning
Initial publication Illustration The covert message is embedded by inserting or changing the temporal/spatial position of a network element (this temporal/spatial position might be described through a virtual element). Original network steganography patterns PT1. Inter-packet Times, PT3. Rate/Throughput, PT13. Frame Collisions, PS2. Sequence, PS2.a. Position, as well as parts of PT11. Message Ordering and PT15./PT16. Artificial Reconnections/Resets. Examples 1) A specific packet sent at some certain point in time in a flow (temporal positioning)
2) Modulating the position of an existing TCP segment in a TCP stream
3) Position of a specific IPv4 option in the list of options Wendzel et al., 2015 as well as the sequence of multiple IPv4 options in the list of options Wendzel et al., 2015, the order of DHCP options Rios et al., 2012 or the order of HTTP header lines Dyatlov and Castro, 2005 or FTP commands Zou et al., 2005 (each element is positioned individually, but overall, they form a sequence)
4) Influencing the inter-arrival time of packets by positioning individual packets Zillien and Wendzel, in press, Cabuk et al., 2004, Cabuk et al., 2009, Shah et al., 2006, Gianvecchio et al., 2008, Zander et al., 2011 (this can also be done to influence the throughput of a connection, e.g., for a switch Li et al., 2011 or a serial communication port Handel et al., 1996).Implementation Zillien and Wendzel, in press R1n1. Network State/Value Modulation
(Derived from E1n1.)
R1.1n1. Network Reserved/Unused State/Value Modulation
(Derived from E1.1n1.)
R1.2n1. Network Random State/Value Modulation
(Derived from E1.2n1.)
R1.3n1. Network LSB State/Value Modulation
(Derived from E1.3n1.)
R1.4n1. Network Character State/Value Modulation
(Derived from E1.4n1.)
R1.5n1. Network Redundancy State/Value Modulation
(Derived from E1.5n1.)
R2n1. Network Element Occurrence
(Derived from E2n1.)
R2.1n1. Network Element Enumeration
(Derived from E2.1n1.)
R2.2n1. Network Element Positioning
(Derived from E2.2n1.)
E1t1. Text State/Value Modulation
Initial publication Illustration The covert message is embedded by modulating the state or value of a text element, such as a paragraph or a character. Examples 1) Overwriting of random characters
2) Modulation of a paragraphs’ or a sentences’ border Stojanov et al., 2014
3) Replacement of some character with a homoglyph (similarly to DNS-based homograph attacks Ravi et al., 2021, in which homoglyphs are used).Implementation E1.2t1. Text Random State/Value Modulation
Initial publication Illustration A (pseudo-)random value or state of/in the text data is replaced with a secret message (that is also following a pseudo-random appearance). Examples Several methods come to mind quickly here as any appearance of (pseudo-)random text strings, such as textual bitstrings, hash values or printed cryp- tographic keys as well as TAN lists for banking and textual nonces can be replaced with steganographic data. Implementation E1.3t1. Text LSB State/Value Modulation
Initial publication Illustration The LSB of text elements are modulated. Examples Modulate the LSBs of a text’s font color (or its R, G and/or B component) Alsaadi et al., 2018 Implementation E1.4t1. Text Character State/Value Modulation
Initial publication Illustration The features of characters in text elements are modulated. Examples 1) All cases in which a textual character’s case is adjusted, e.g., in text files, source code, HTML files etc.
2) Modulation of a characters’ glyph Xiao et al., 2017, underlining Stojanov et al., 2014, font type Bhaya et al., 2013, color or luminance intensity (color quantization) Villán et al., 2006.Implementation E1.5t1. Text Redundancy State/Value Modulation
Initial publication Illustration The redundancy of a text element’s content is modulated (this is usually applied by a succeeding pattern that fills the gained space with covert data), e.g., by means of semantic-preserving compression. Examples All semantic methods that include synonym substitution Chapman et al., 2001, paraphrasing Jin et al., 2010, changing word spelling Shirali-Shahreza, 2008, using of abbreviations and acronyms with typographical errors Topkara et al., 2007, etc. belong in this pattern. In general, the semantics of texts can be kept, even if shortened. For instance, the sentence “This very moment can be considered relevant.” can also be expressed in a shorter form: “This moment is relevant.”. Implementation E2t1. Text Element Occurrence
Initial publication Illustration The covert message is encoded in the spatial or temporal location of elements, which can also, e.g., influence the rate or overall number of text elements appearing in a message flow (succeeding messages occur shortly or long after the previous ones). Examples 1) All syntactic methods that include changing the diction and structure of text without significantly altering meaning or tone, by means of punctuation Bender et al., 1996, shifting the location of the noun and verb Murphy and Vogel, 2007, pointed letters and extensions in Arabic language Gutub and Fattani, 2007, etc., belong here
2) Selecting one out of multiple plausible HTML tags to set a character in bold font (e.g.<b>vs.<strong>) Dyatlov and Castro, 2005
3) Removing commas in sentences (i.e., the elements do not appear) Bender et al., 1996
4) Use of emoticons and/or lingoes for hiding data in SMS and chats Wang et al., 2006, Iranmanesh et al., 2015.Implementation E2.1t1. Text Element Enumeration
Initial publication Illustration An attribute describing the quantity of text sub-elements is modulated. This pattern also applies if sub-elements are added to a textual element to increase its overall size (e.g., by adding more characters to a text so that the overall length of the text is influenced). Examples 1) Repeating a white space element (or any Unicode space character) by duplicating it (or not) in a text (open space method) Bender et al., 1996, Por et al., 2012
2) Adding/removing tags in an HTML file (e.g., to influence the overall number of tags).Implementation E2.2t1. Text Element Positioning
Initial publication Illustration The covert message is embedded by inserting or changing the temporal/spatial position of a text element (this temporal/spatial position might be described through a virtual element) Examples 1) A character of text placed at some particular location (spatial positioning)
2) Placing a specific HTML tag’s attribute in the list of attributes, e.g.,<img text=‘‘..." src=‘‘..." alt=‘‘..." />
vs.<img alt=‘‘..." text=‘‘..." src=‘‘..." />
3) Line and word shift coding Brassil et al., 1995, Low et al., 1995
4) Combining specific invisible Unicode characters to represent different groups of 𝑛 secret bits Odeh et al., 2014.Implementation E2t1.1. Generative Text Element Occurrence
Initial publication Illustration There is one group of text steganographic methods that are identified with the umbrella term “generative linguistic steganography” (or random and statistical methods Ahvanooey et al., 2019). These can be considered a special variant of E2t1. Text Element Occurrence and are thus categorized as E2t1.1.. In essence, such methods directly transform the secret data into steganographic text, without any cover text, by using natural language models. To this aim, they first use a known model to learn the statistical language model from a large set of natural language sentences, and then they embed the secret data by encoding the conditional probability distribution of each word in the cover text generation process. Examples This pattern can be realized by neural networks (e.g., Long Short-Term Memory - LSTM Fang et al., 2017, Recurrent Neural Networks - RNN Yang et al., 2018, Generative Adversarial Networks - GAN Yang et al., 2019), discrete random processes (e.g., Markov chain model Wu et al., 2020), and Context-Free-Grammars Chapman and Davida, 1997, just to mention some. Implementation R1t1. Text State/Value Modulation
(Derived from E1t1.)
R1.2t1. Text Random State/Value Modulation
(Derived from E1.2t1.)
R1.3t1. Text LSB State/Value Modulation
(Derived from E1.3t1.)
R1.4t1. Text Character State/Value Modulation
(Derived from E1.4t1.)
R1.5t1. Text Redundancy State/Value Modulation
(Derived from E1.5t1.)
R2t1. Text Element Occurrence
(Derived from E2t1.)
R2.1t1. Text Element Enumeration
(Derived from E2.1t1.)
R2.2t1. Text Element Positioning
(Derived from E2.2t1.)
R2t1.1. Generative Text Element Occurrence
(Derived from E2t1.1.)
An early, but still good, reference providing details on most of the example techniques discussed below is Johnson and Katzenbeisser, 2000.
E1d1. Digital Media State/Value Modulation
Initial publication Illustration The covert message is embedded by modulating the state or value of a digital media element, such as a pixel, video frame or sound sample. Examples 1) LSB embedding
2) Echo hiding for audio signals, utilizing (artificially created) echo components, where the data is usually hidden by varying characteristics of the echo such as the amplitude, decay cost and offset or delay
3) Spread spectrum techniques
4) Manipulating the phase coding for consecutive frames in an audio signal.Implementation E1.1d1 Digital Media Reserved/Unused State/Value Modulation
Initial publication Illustration The covert message is embedded by modulating reserved/unused states/values of digital media elements. Examples Embedding message parts into media blocks that are not used/rendered in the playback/rendering process, such as non-referenced content chunks in PNG or PDF files. Implementation E1.2d1. Digital Media Random State/Value Modulation
Initial publication Illustration A (pseudo-)random value or state of/in digital media data is replaced with a secret message (that is also following a pseudo-random appearance) Examples In spread spectrum audio steganography the message is usually encoded into a pseudo-random bit-string which is in the embedding spread as much as applicable over the frequency spectrum, forming a low-amplitude ‘background noise’. Implementation E1.3d1. Digital Media LSB State/Value Modulation
Initial publication Illustration The LSB of digital media elements are modulated. Examples Low-bit encoding using the least significant bit plane of a media representation is a technique used in many different media formats, including raster images and audio files. Implementation E1.4d1. Digital Media Character State/Value Modulation
Initial publication Illustration The features of characters in digital media elements are modulated. Examples This pattern was rarely found to be represented in the literature. However, one notable example is the following:
Manipulation of the duration of notes in a MIDI audio file in Guan et al., 2019.Implementation E1.5d1. Digital Media Redundancy State/Value Modulation
Initial publication Illustration The redundancy of a digital media element’s content is modulated (this is usually applied by a succeeding pattern that fills the gained space with covert data), e.g., by means of compression. Examples 1) Quantization index modulation in media compression operations, e.g., in MP3 compression (e.g., see Qiao et al., 2009)
2) Exploiting the correlation/redundancy between both audio channels in stereo signals.Implementation E2d1. Digital Media Element Occurrence
Initial publication Illustration The covert message is encoded in the spatial or temporal location of elements, which can also, e.g., influence the rate or overall number of digital media elements appearing in a flow (succeeding messages occur shortly or long after previous ones). Examples 1) Influence the rate of acoustic beeps appearing in an audio file
2) Influence the particular location of a pixel with a specific color in a digital image.Implementation E2.1d1. Digital Media Element Enumeration
Initial publication Illustration An attribute describing the quantity of digital media subelements is modulated. This pattern also applies if sub-elements are added to a digital media element to increase the overall length of the element (e.g., by adding more pixels to a digital image file). Examples 1) Influence the number of succeeding beeps in an audio file
2) Influence the number of succeeding pixels with the same value or the overall number of pixels in a file.Implementation E2.2d1. Digital Media Element Positioning
Initial publication Illustration The covert message is embedded by inserting or changing the temporal/spatial position of a digital media element (this temporal/spatial position might be described through a virtual element). Examples This pattern is rarely represented through existing methods. However, one example could be
1) The embedding of a blue screen frame at a specific location in a video file.Implementation R1d1. Digital Media State/Value Modulation
(Derived from E1d1.)
R1.1d1. Digital Media Reserved/Unused State/Value Modulation
(Derived from E1.1d1.)
R1.2d1. Digital Media Random State/Value Modulation
(Derived from E1.2d1.)
R1.3d1. Digital Media LSB State/Value Modulation
(Derived from E1.3d1.)
R1.4d1. Digital Media Character State/Value Modulation
(Derived from E1.4d1.)
R1.5d1. Digital Media Redundancy State/Value Modulation
(Derived from E1.5d1.)
R2d1. Digital Media Element Occurrence
(Derived from E2d1.)
R2.1d1.
(Derived from E2.1d1.)
R2.2d1. Digital Media Element Enumeration
(Derived from E2.2d1.)
E1c1. CPS State/Value Modulation
Initial publication Illustration The covert message is embedded by modulating the state or value of a CPS element, such as an actuator state or values in unused elements. Examples 1) Modulation of actuator states Wendzel et al., 2017
2) Modulation of a setpoint in a control command
3) Modulation of ICS configuration data (and its backups) for long-term storage of secret data Hartmann and Wendzel, 2021
4) Modulation of control action states in the controller logic Abdelwahab et al., 2021
5) Modulation of control signal and state measurements Abdelwahab et al., 2021.Implementation E1.1c1. CPS Reserved/Unused State/Value Modulation
Initial publication Illustration The covert message is embedded by modulating reserved/unused states/values of CPS elements. Examples 1) Modulation of values in unused registers of embedded CPS equipment Wendzel et al., 2017
2) Modulation of values in unused bits of control commandsImplementation E1.2c1. CPS Random State/Value Modulation
Initial publication Illustration A (pseudo-)random value or state of/in CPS or its data is replaced with a secret message (that is also following a pseudo-random appearance). Examples 1) Overwrite a randomized order of colors in a (smart home) light show
2) Exploit MAC address randomization of an Android smartphone (here considered as a cyber-physical device due to its sensors and actuators) to overwrite it with a secret message
3) An imaginable idea is to replace the randomized bits of the ShadowAuth CAN authentication message with encrypted covert data (cf. Kim et al., 2022)
4) One could potentially apply the idea of replacement of entries in a conditioner buffer from physical processes used in an RNG similarly as described by a work of Evtyushkin et al., 2016, where the buffer is first replaced by rseeds, followed by an entry that is replaced by the sender or not
5) Modulation of high-resolution sensor values affected by random sensor- and/or process noise (c.f. Lamshöft et al., 2021, Herzberg and Kfir, 2019).Implementation E1.3c1. CPS LSB State/Value Modulation
Initial publication Illustration The LSB of CPS elements are modulated. Examples 1) Modulate the LSB for a setpoint of an actuator (e.g., a motor’s RPM)
2) Alter the history of stored LSBs of temperature sensor values to encode one bit per logged temperature value.Implementation E1.4c1. CPS Character State/Value Modulation
Initial publication Illustration The features of characters in CPS elements are modulated. This pattern is essentially an application of text steganography methods to the CPS context. It is kept for completeness. Examples 1) Capitalizing every 𝑛th character of a variable’s, project’s, or device’s name
2) Changing font color or size of a comment in a code block in the TIA (a configuration and management software for industrial control systems) Portal settings.Implementation E1.5c1. CPS Redundancy State/Value Modulation
Initial publication Illustration The redundancy of a CPS element’s content is modulated (this is usually applied by a succeeding pattern that fills the gained space with covert data), e.g., by means of compression. Examples 1) Renaming TIA projects, e.g., from “RTP020” to “soldering tip version RTP020”
2) Modulate the behavior of an ICS so that it either moves to its default position before proceeding with the next work piece or directly proceeds with that piece.Implementation E2c1. CPS Element Occurrence
Initial publication Illustration The covert message is encoded in the spatial or temporal location of elements, which can also, e.g., influence the rate or overall number of CPS elements appearing in a sequence (succeeding messages occur shortly or long after previous ones). Examples 1) Influence the point in time at which a certain cyber-physical action is performed (e.g., opening/closing a window)
2) Writing deduplication records into the ICSs’ filesystem to exfiltrate secret data Bacs et al., 2022.Implementation E2.1c1. CPS Element Enumeration
Initial publication Illustration An attribute describing the quantity of CPS sub-elements is modulated. This pattern also applies if sub-elements are added to a CPS element to increase its overall size (e.g., by adding more configuration parameters to a CPS configuration). Examples 1) Modulating the number of windows that are opened succeedingly
2) Modulating the number of setpoints accumulated within a single control command (e.g., using BACnet’s WriteMultiple command).Implementation E2.2c1. CPS Element Positioning
Initial publication Illustration The covert message is embedded by inserting or changing the temporal/spatial position of a CPS element (this temporal/spatial position might be described through a virtual element). Examples 1) Influencing the location of a drone (e.g., so that its current location or a whole path represents a secret message)
2) Modulate the position in time of a specific sensor reading operation (alternatively, succeeding read operations could be timed, e.g., to influence the time between commands which then can be observed by the CR)
3) Raising the sampling frequency of sensor multiplexing in Android smartphones at a specific temporal position to transmit a secret message Shepherd et al., 2021
4) Switching between on and off state of a vibration motor in a smartphone in a specific temporal order Al-Haiqi et al., 2014
5) Modulation of actuator response time (required time to change its state) Herzberg and Kfir, 2019.Implementation R1c1. CPS State/Value Modulation
(Derived from E1c1.)
R1.1c1. CPS Reserved/Unused State/Value Modulation
(Derived from E1.1c1.)
R1.2c1. CPS Random State/Value Modulation
(Derived from E1.2c1.)
R1.3c1. CPS LSB State/Value Modulation
(Derived from E1.3c1.)
R1.4c1. CPS Character State/Value Modulation
(Derived from E1.4c1.)
R1.5c1. CPS Redundancy State/Value Modulation
(Derived from E1.5c1.)
R2c1. CPS Element Occurrence
(Derived from E2c1.)
R2.1c1. CPS Element Enumeration
(Derived from E2.1c1.)
R2.2c1. CPS Element Positioning
(Derived from E2.2c1.)
E1f1. Filesystem State/Value Modulation
Initial publication Illustration The covert message is embedded by modulating the state or value of a filesystem element, such as a file/inode attribute. Examples 1) Similar to text steganography, replace a character of a textual filename with its homoglyph Woodbridge et al., 2018
2) Embed secret data in unused/reserved or random-value meta-data fields Huebner et al., 2006
3) Modulate timestamp values Neuner et al., 2016
4) Case modulation of filename characters.Implementation E1.1f1. Filesystem Reserved/Unused State/Value Modulation
Initial publication Illustration The covert message is embedded by modulating reserved/unused states/values of filesystem elements. Examples 1) Placing secret data in bytes of unused blocks Han et al., 2010, McDonald and Kuhn, 1999, Barker et al., 2019
2) Hide secret information in the metadata of deleted (now unused) files of the exFAT filesystem Heeger et al., 2021.Implementation E1.2f1. Filesystem Random State/Value Modulation
Initial publication Illustration A (pseudo-)random value or state of/in a filesystem or its sub-elements is replaced with a secret message (that is also following a pseudo-random appearance). Examples 1) In their seminal paper that introduced filesystem steganography, Anderson et al., 1998 superimposed hidden files onto files with random (or randomly looking, e.g., encrypted) content
2) Similarly to the examples of E1.1f1, already allocated blocks that contain a high entropy (pseudo-random content) can be overwritten for steganographic storage Pang et al., 2003 (instead of unused blocks).Implementation E1.3f1. Filesystem LSB State/Value Modulation
Initial publication Illustration The LSB of filesystem elements are modulated. Examples 1) Modulation of the nanoseconds bits in the NTFS access/creation time attribute of a file Neuner et al., 2016
2) Modulation of the least significant bits of the exFAT fieldsCreatE1msIncrementandLastModified10msIncrementHeeger et al., 2021.Implementation E1.4f1. Filesystem Character State/Value Modulation
Initial publication Illustration The features of characters in filesystem elements are modulated. Examples 1) Given the support of a particular filesystem for upper- and lower-case characters, filename characters’ cases can be modulated. This method can be applicable in all cases where both the covert sender and receiver have visibility over files. For instance, this approach has been used to transmit data remotely in Dropbox, e.g., modulation of names propagates through a shared folder to create a network covert channel Caviglione et al., 2017
2) Replacement of characters in filenames with homoglyphs.Implementation E2f1. Filesystem Element Occurrence
Initial publication Illustration The covert message is encoded in the spatial or temporal location of elements, which can also, e.g., influence the rate or overall number of filesystem elements appearing in a sequence (succeeding messages occur shortly or long after previous ones). Examples 1) Let a certain filename appear (or not) to encode a hidden message
2) Modulate the number of files or inodes in a filesystem
3) Position filesystem elements in a temporal or spatial order.Implementation E2.1f1. Filesystem Element Enumeration
Initial publication Illustration An attribute describing the quantity of filesystem subelements is modulated. This pattern also applies if subelements are added to a filesystem element to increase its overall size (e.g., by adding more files to a directory to increase the overall directory’s length). Examples Modulate the number of inodes/files in a filesystem or the number of bytes within a file (influences file size/number of allocated blocks) to encode a secret message Chang et al., 2015. Implementation E2.2f1. Filesystem Element Positioning
Initial publication Illustration The covert message is embedded by inserting or changing the temporal/spatial position of a filesystem element (this temporal/spatial position might be described through a virtual element). Examples 1) Modulate the order of multiple file create() operations to influence their order of appearance in file managers (e.g., permutation steganography for FAT Aycock and Castro, 2015)
2) Write to even/odd FAT cluster4 locations, depending on the bit value (and derivations of this approach) Khan et al., 2011.Implementation R1f1. Filesystem State/Value Modulation
(Derived from E1f1.)
R1.1f1. Filesystem Reserved/Unused State/Value Modulation
(Derived from E1.1f1.)
R1.2f1. Filesystem Random State/Value Modulation
(Derived from E1.2f1.)
R1.3f1. Filesystem LSB State/Value Modulation
(Derived from E1.3f1.)
R1.4f1. Filesystem Character State/Value Modulation
(Derived from E1.4f1.)
R2f1. Filesystem Element Occurrence
(Derived from E2f1.)
R2.1f1. Filesystem Element Enumeration
(Derived from E2.1f1.)
R2.2f1. Filesystem Element Positioning
(Derived from E2.2f1.)
Bibliography:
Steffen Wendzel, Sebastian Zander, Bernhard Fechner, and Christian Herdin: Pattern-based Survey and Categorization of Network Covert Channels, ACM Comp. Surv., 2015.
Sebastian Zillien, Steffen Wendzel: Weaknesses of popular and recent covert channel detection methods and a remedy, IEEE Trans. Dependable and Secure Computing (TDSC), in press.
Liping Ji, Yu Fan, and Chuan Ma: Covert channel for local area network, 2010 IEEE International Conference on Wireless Communications, Networking and Information Security, pages 316-319, 2010.
Norka B. Lucena, Grzegorz Lewandowski, and Steve J. Chapin: Covert channels in IPv6, International Workshop on Privacy Enhancing Technologies, Springer, pages 147-166. 2005.
Theodore G. Handel and Maxwell T. Sandford II, Hiding data in the OSI network model, in Proceedings of the 1st International Workshop on Information Hiding, 1996, pp. 23–38.
Manfred Wolf, Covert channels in LAN protocols, in Proc. Local Area Network Security, ser. LNCS. Springer, 1989, vol. 396, pp. 89–101.
Bartosz Jankowski, Wojciech Mazurczyk, and Krzysztof Szczypiorski, Information hiding using improper frame padding, eprint arXiv:1005.1925, 2010.
Ahmad-Reza Sadeghi, Steffen Schulz, and Vijay Varadharajan, The silence of the lans: Efficient leakage resilience for IPsec VPNs, in Computer Security – ESORICS 2012, ser. LNCS, vol. 7459. Springer Berlin Heidelberg, 2012, pp. 253–270.
Daniel Stødle, Ping tunnel – for those times when everything else is blocked, 2009.
daemon9, LOKI2 (the implementation), Phrack Magazine, vol. 7, no. 51, 1997.
Steffen Wendzel, Benjamin Kahler, and Thomas Rist, Covert channels and their prevention in building automation protocols: A prototype exemplified using BACnet, in Proc. 2012 Int. Conf. Green Computing and Communications (GreenCom). IEEE, 2012, pp. 731–736.
Ruben Rios, Jose A. Onieva, and Javier Lopez, HIDE DHCP: Covert communications through network configuration messages, in Proc. IFIP TC 11 27th International Information Security Conference. Springer, 2012.
Aleksandar Velinov, Aleksandra Mileva, Steffen Wendzel, and Wojciech Mazurczyk, Covert channels in MQTT-based internet of things, ACCESS, vol. 7, 2019, pp. 161 899–161 915.
Wojciech Mazurczyk and Krzysztof Szczypiorski, Covert Channels in SIP for VoIP signalling, Springer, 2008, pp. 65–72.
Craig H. Rowland, Covert channels in the TCP/IP protocol suite, First Monday, vol. 2, no. 5, May 1997.
Joanna Rutkowska, The implementation of passive covert channels in the Linux kernel, 2004, speech held at the 21st Chaos Communication Congress, Berlin, Germany.
Norka B. Lucena, James Pease, Payman Yadollahpour, and Steve J. Chapin, Syntax and semantics-preserving application-layer protocol steganography, in Proceedings of 6th Information Hiding Workshop, May 2004.
Tobias Schmidbauer, Steffen Wendzel, and Jörg Keller, Challenging channels: Encrypted covert channels within challenge-response authentication, in Proceedings of the 17th International Conference on Availability, Reliability and Security (ARES), 2022, in press.
John Giffin, Rachel Greenstadt, Peter Litwack, and Richard Tibbetts, Covert messaging through TCP timestamps, in Proc. 2nd International Conference on Privacy Enhancing Technologies. Springer, 2003, pp. 194–208.
Reshad Patuck and Julio Hernandez-Castro, Steganography using the extensible messaging and presence protocol (XMPP), CoRR, vol. abs/1310.0524, 2013.
Giuseppe Bernieri, Stefano Cecconello, Mauro Conti, and Gianluca Lain, TAMBUS: A novel authentication method through covert channels for securing industrial networks, Computer Networks, vol. 183, 2020, p. 107583.
Alex Dyatlov and Simon Castro, Exploitation of data streams authorized by a network access control system for arbitrary data transfers: tunneling and covert channels over the HTTP protocol, Gray-World.net, Tech. Rep., 2005.
Wojciech Mazurczyk, Steffen Wendzel, and Krzysztof Cabaj, Towards deriving insights into data hiding methods using pattern-based approach, in Proc. Second International Workshop on Criminal Use of Information Hiding (CUING 2018), part of Proc. ARES’18. ACM, 2018, pp. 10:1–10:10.
Wojciech Mazurczyk, Paweł Szaga, and Krzysztof Szczypiorski, Using transcoding for hidden communication in IP telephony, Multimedia Tools Appl., vol. 70, no. 3, 2014, pp. 2139–2165.
Sabine S. Schmidt, Wojciech Mazurczyk, Jörg Keller, and Luca Caviglione, A new data-hiding approach for IP telephony applications with silence suppression, in Proceedings of the 12th International Conference on Availability, Reliability and Security, 2017, pp. 1–6.
Bartosz Jankowski, Wojciech Mazurczyk, and Krzysztof Szczypiorski, PadSteg: Introducing inter-protocol steganography, Telecommunication Systems, vol. 52, no. 2, 2013, pp. 1101–1111.
Christian Kraetzer, Jana Dittmann, Andreas Lang, and Tobias Kuehne, WLAN steganography: A first practical review, in Proc. 8th Workshop on Multimedia and Security (MMSEC’06), 2006, pp. 17–22.
Sebastian Zillien and Steffen Wendzel, Detection of covert channels in TCP retransmissions, in Secure IT Systems, N. Gruschka, Ed. Cham: Springer International Publishing, 2018, pp. 203–218.
X. Li, Y. Zhang, F. Chong, and B. Zhao, “A covert channel analysis of a real switch”, Dep. of Computer Science, University of California, Santa Barbara, Tech. Rep., 2011.
Wojciech Mazurczyk, Milosz Smolarczyk, and Krzysztof Szczypiorski, Retransmission steganography and its detection, Soft Computing, vol. 15, no. 3, 2011, pp. 505–515.
Wojciech Mazurczyk and Krzysztof Szczypiorski, Evaluation of steganographic methods for oversized IP packets, Telecommunication Systems, vol. 49, no. 2, 2012, pp. 207–217.
Xin-guang Zou, Qiong Li, Sheng-He Sun, and Xiamu Niu, The research on information hiding based on command sequence of FTP protocol, in Proc. 9th Int. Conf. on Knowledge-Based Intelligent Information and Engineering Systems (KES 2005), Part III, ser. LNCS, vol. 3683. Springer Berlin Heidelberg, 2005, pp. 1079–1085.
Abe Getchell, Re: For those interested in covert channels, 2008, a posting on the securityfocus penetration testing mailinglist.
Thomas Graf, “Messaging over IPv6 destination options”, 2003, swiss Unix User Group.
Serdar Cabuk, Carla E. Brodley, and Clay Shields, IP covert timing channels: design and detection, in Proceedings of the 11th ACM conference on Computer and communications security, ser. CCS ‘04. New York, NY, USA: ACM, 2004, pp. 178–187.
Serdar Cabuk, Carla E. Brodley, and Clay Shields, IP covert channel detection, ACM Transactions on Information and System Security (TISSEC), vol. 12, no. 4, April 2009, pp. 22:1–22:29.
Gaurav Shah, Andres Molina, and Matt Blaze, Keyboards and covert channels, in Proc. 15th USENIX Security Symposium. USENIX Association, 2006, pp. 59–75.
Steven Gianvecchio, Haining Wang, Duminda Wijesekera, and Sushil Jajodia, Model-based covert timing channels: Automated modeling and evasion, in Proceedings of Recent Advances in Intrusion Detection (RAID) Symposium, September 2008.
Sebastian Zander, Grenville J. Armitage, and Philip Branch, Stealthier inter-packet timing covert channels, in IFIP Networking. Springer Berlin Heidelberg, May 2011, pp. 458–470.
I. Stojanov, A. Mileva, and I. Stojanovic, A new property coding in text steganography of microsoft word documents, in Proceedings of SECURWARE 2014: The Eighth International Conference on Emerging Security Information, Systems and Technologies, November 2014, pp. 25–30.
V. Ravi, M. Alazab, S. Srinivasan, A. Arunachalam, and K. Soman, Adversarial defense: DGA-based botnets and DNS homographs detection through integrated deep learning IEEE Transactions on Engineering Management, 2021.
H. Alsaadi, M. Al-Anni, R. Almuttairi, O. Bayat, and O. Ucan, Text steganography in font color of MS Excel sheet in DATA ‘18: Proceedings of the First International Conference on Data Science, E-learning and Information Systems, 2018, pp. 1–7.
C. Xiao, C. Zhang, and C. Zheng, FontCode: embedding information in text documents using glyph perturbation in ACM Transactions on Graphics, vol. 1, no. 1, December 2017.
W. Bhaya, A. M. Rahma, and D. Al-Nasrawi, Text steganography based on font type in MS-Word documents in Journal of Computer Science, vol. 9, no. 7, 2013, pp. 898—-904.
R. Villán, S. Voloshynovskiy, O. Koval, J. Vila, E. Topak, F. Deguillaume, Y. Rytsar, and T. Pun, Text data-hiding for digital and printed documents: Theoretical and practical considerations in Proceedings of the SPIE Electronic Imaging: Security, Steganography, and Watermarking of Multimedia Contents VIII, vol. 6072, 2006.
M. Chapman, G. Davida, and M. Rennhard, A practical and effective approach to largescale automated linguistic steganography in Proceedings of the Information Security Conference (ISC ‘01), 2001, pp. 156–156.
C. Jin, D. Zhang, and M. Pan, Chinese text information hiding based on paraphrasing technology in Proceedings of the International Conference on Information Science and Management Engineering (ISME2010), vol. 1, 2010.
M. Shirali-Shahreza, Text steganography by changing words spelling in Proceedings of the 10th International Conference on Advanced Communication Technology (ICACT 2008), vol. 3, 2008, pp. 1912–1913.
M. Topkara, U. Taskiran, and M. J. Atallah, Information Hiding Through Errors: A Confusing Approach in Proceedings of the SPIE Electronic Imaging: Security, Steganography, and Watermarking of Multimedia Contents IX, vol. 6505, 2007.
W. Bender, D. Gruhl, N. Morimoto, and A. Lu, Techniques for data hiding IBM Systems Journal, vol. 35 (Nos3&4), 1996, pp. 313–336.
B. Murphy and C. Vogel, The syntax of concealment: reliable methods for plain text information hiding in Proceedings of the SPIE Electronic Imaging: Security, Steganography, and Watermarking of Multimedia Contents IX, vol. 6505, 2007.
A. Gutub and M. Fattani, A novel arabic text steganography method using letter points and extensions in Proceedings of the WASET International Conference on Computer, Information and Systems Science and Engineering (ICCISSE), vol. 21, 2007, pp. 28—-31.
Z.-H. Wang, T. D. Kieu, C.-C. Chang, and M.-C. Li, Emoticon-based text steganography in chat in Asia-Pacific Conference on Computational Intelligence and Industrial Applications (PACIIA), 2009, pp. 457–460.
V. Iranmanesh, H. J. Wei, S. L. Dao-Ming, and O. A. Arigbabu, On using emoticons and lingoes for hiding data in SMS in International Symposium on Technology Management and Emerging Technologies (ISTMET), 2015, pp. 103–107.
L. Y. Por, K. Wong, and K. O. Chee, UniSpaCh: A text-based data hiding method using unicode space characters Journal of Systems and Software, vol. 85, 2012, pp. 1075–1082.
T. Brassil, S. Low, N. Maxemchuk, and L. O‘Gorman, Electronic marking and identification techniques to discourage document copying IEEE Journal on Selected Areas in Communications, vol. 13, no. 8, 1995, pp. 1495–1504.
S. H. Low, N. F. Maxemchuk, J. T. Brassil, and L. O‘Gorman, Document marking and identification using both line and word shifting in Proceedings of the 14th Annual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM ‘95), April 1995, pp. 853—-860.
A. Odeh, K. Elleithy, and M. Faezipour, Steganography in text by using MS Word symbols in Proceedings of the 2014 Zone 1 Conference of the American Society for Engineering Education, 2014.
M. T. Ahvanooey, Q. Li, J. Hou, A. R. Rajput, and Y. Chen, Modern text hiding, text steganalysis, and applications: A comparative analysis in Entropy, vol. 21, no. 4, 2019, p. 355.
T. Fang, M. Jaggi, and K. Argyraki, Generating steganographic text with LSTMs in Proceedings of ACL 2017, Student Research Workshop, 2017, pp. 100–106.
Z.-L. Yang, X.-Q. Guo, Z.-M. Chen, Y.-F. Huang, and Z. Y.-J., RNN-Stega: Linguistic steganography based on recurrent neural networks IEEE Transactions on Information Forensics and Security, vol. 14, no. 5, 2018, pp. 1280–1295.
Z. Yang, N. Wei, Q. Liu, Y. Huang, and Y. Zhang, GAN-TStega: text steganography based on generative adversarial networks in Digital Forensics and Watermarking (IWDW 2019), LNCS, vol. 12022. Springer, Cham, 2019.
N. Wu, Z. Yang, Y. Yang, L. Li, P. Shang, W. Ma, and Z. Liu, STBS-Stega: Coverless text steganography based on state transition-binary sequence International Journal of Distributed Sensor Networks, vol. 16, no. 3, 2020.
M. Chapman and G. Davida, Hiding the hidden: A software system for concealing ciphertext as innocuous text in International Conference on Information and Communications Security, 1997, pp. 335–345.
N. F. Johnson and S. Katzenbeisser, A survey of steganographic techniques in Information hiding, 2000, pp. 43–78.
L. Guan, Y. Jing, S. Li, and R. Zhang, A standard MIDI file steganography based on music perception in note duration in Proceedings of the 6th Conference on Sound and Music Technology (CSMT), W. Li, S. Li, X. Shao, and Z. Li, Eds. Singapore: Springer Singapore, 2019, pp. 99–107.
M. Qiao, A. Sung, and Q. Liu, Steganalysis of MP3Stego 06 2009, pp. 2566–2571.
S. Wendzel, W. Mazurczyk, and G. Haas, Don’t you touch my nuts: Information hiding in cyber physical systems in IEEE Security and Privacy Workshops (SPW’17). IEEE, 2017, pp. 29–34.
L. Hartmann and S. Wendzel, How feasible are steganographic and stealth attacks on TIA project meta-data of ICS: A case study with real-world data in Proc. European Interdisciplinary Cybersecurity Conference (EICC 2021). ACM, 2021.
A. Abdelwahab, W. Lucia, and A. Youssef, Covert channels in cyberphysical systems IEEE Control Systems Letters, vol. 5, no. 4, 2021, pp. 1273–1278.
S. Kim, G. Yeo, T. Kim, J. J. Rhee, Y. Jeon, A. Bianchi, D. Xu, and D. J. Tian, ShadowAuth: Backward-compatible automatic CAN authentication for legacy ECUs in Proc. 2022 ACM on Asia Conference on Computer and Communications Security, ser. ASIA CCS ‘22. New York, NY, USA: Association for Computing Machinery, 2022, p. 534–545.
D. Evtyushkin and D. Ponomarev, Covert channels through random number generator: Mechanisms, capacity estimation and mitigations in Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, ser. CCS ‘16. New York, NY, USA: Association for Computing Machinery, 2016, p. 843–857.
K. Lamshöft, T. Neubert, C. Krätzer, C. Vielhauer, and J. Dittmann, Information hiding in cyber physical systems: Challenges for embedding, retrieval and detection using sensor data of the SWAT dataset in Proceedings of the 2021 ACM Workshop on Information Hiding and Multimedia Security, ser. IH&MMSec ‘21. New York, NY, USA: Association for Computing Machinery, 2021, p. 113–124.
A. Herzberg and Y. Kfir, The chatty-sensor: A provably-covert channel in cyber physical systems in Proceedings of the 35th Annual Computer Security Applications Conference, ser. ACSAC ‘19. New York, NY, USA: Association for Computing Machinery, Dec. 2019, pp. 638–649.
A. Bacs, S. Musaev, K. Razavi, C. Giuffrida, and H. Bos, DUPEFS: Leaking data over the network with filesystem deduplication side channels in 20th USENIX Conference on File and Storage Technologies (FAST 22). Santa Clara, CA: USENIX Association, Feb. 2022, pp. 281–296.
C. Shepherd, J. Kalbantner, B. Semal, and K. Markantonakis, A side-channel analysis of sensor multiplexing for covert channels and application fingerprinting on mobile devices 2021.
A. Al-Haiqi, M. Ismail, and R. Nordin, A new sensors-based covert channel on Android vol. 2014, no. 969628, 2014.
A. Herzberg and Y. Kfir, The Leaky Actuator: A Provably-covert Channel in Cyber Physical Systems in Proceedings of the ACM Workshop on Cyber-Physical Systems Security & Privacy, ser. CPS-SPC’19. New York, NY, USA: Association for Computing Machinery, Nov. 2019, pp. 87–98.
J. Woodbridge, H. S. Anderson, A. Ahuja, and D. Grant, Detecting homoglyph attacks with a siamese neural network in 2018 IEEE Security and Privacy Workshops (SPW). IEEE, 2018, pp. 22–28.
E. Huebner, D. Bem, and C. K. Wee, Data hiding in the NTFS file system Digit. Investig., vol. 3, no. 4, 2006, pp. 211–226.
S. Neuner, A. G. Voyiatzis, M. Schmiedecker, S. Brunthaler, S. Katzenbeisser, and E. R. Weippl, Time is on my side: Steganography in filesystem metadata Digital Investigation, vol. 18, 2016, pp. S76–S86.
J. Han, M. Pan, D. Gao, and H. Pang, A multi-user steganographic file system on untrusted shared storage in Twenty-Sixth Annual Computer Security Applications Conference, ACSAC 2010, Austin, Texas, USA, 6-10 December 2010, C. Gates, M. Franz, and J. P. McDermott, Eds. ACM, 2010, pp. 317–326.
A. D. McDonald and M. G. Kuhn, StegFS: A steganographic file system for Linux in International Workshop on Information Hiding. Springer, 1999, pp. 463–477
A. Barker, S. Sample, Y. Gupta, A. McTaggart, E. L. Miller, and D. D. E. Long, Artifice: A deniable steganographic file system in 9th USENIX Workshop on Free and Open Communications on the Internet, FOCI 2019, Santa Clara, CA, USA, August 13, 2019, S. E. McGregor and M. C. Tschantz, Eds. USENIX Association, 2019.
J. Heeger, Y. Yannikos, and M. Steinebach, ExHide: Hiding data within the ExFAT file system in The 16th International Conference on Availability, Reliability and Security, ser. ARES 2021. New York, NY, USA: Association for Computing Machinery, 2021.
R. J. Anderson, R. M. Needham, and A. Shamir, The steganographic file system in Information Hiding, Second International Workshop, Portland, Oregon, USA, April 14-17, 1998, Proceedings, ser. Lecture Notes in Computer Science, D. Aucsmith, Ed., vol. 1525. Springer, 1998, pp. 73–82.
H. Pang, K.-L. Tan, and X. Zhou, StegFS: A steganographic file system in Proceedings 19th International Conference on Data Engineering (Cat. No. 03CH37405). IEEE, 2003, pp. 657–667.
L. Caviglione, M. Podolski, W. Mazurczyk, and M. Ianigro, Covert channels in personal cloud storage services: The case of Dropbox IEEE Transactions on Industrial Informatics, vol. 13, no. 4, 2017, pp. 1921–1931.
B. Chang, Z. Wang, B. Chen, and F. Zhang, MobiPluto: File system friendly deniable storage for mobile devices in Proceedings of the 31st Annual Computer Security Applications Conference, Los Angeles, CA, USA, December 7-11, 2015. ACM, 2015, pp. 381–390.
J. Aycock and D. M. N. de Castro, Permutation steganography in FAT filesystems Transactions on Data Hiding and Multimedia Security X, vol. 8948, 2015, pp. 92–105.
H. Khan, M. Javed, S. A. Khayam, and F. Mirza, Designing a cluster-based covert channel to evade disk investigation and forensics Computers & Security (COAS), vol. 30, no. 1, 2011, pp. 35–49.