Glossary
Please note that the following content is extracted from our paper that can be cited as follows:
- S. Wendzel, L. Caviglione, W. Mazurczyk, A. Mileva, J. Dittmann, C. Krätzer, K. Lamshöft, C. Vielhauer, L. Hartmann, J. Keller, T. Neubert, S. Zillien (2022): A Generic Taxonomy for Steganography Methods, pre-print, 2022.
Even if the creation of an exhaustive, non-ambiguous vocabulary for steganographic applications is outside the scope of this work, reducing possible confusions or overloading of terms is fundamental to not void the efficiency and expressiveness of the taxonomy. Specifically, the term modifiable object we define as the general object type that will be used to contain or represent the secret information. The process of hiding data within the cover depends on the mechanism or pattern used. In the following, we refer to such a process as embedding, injecting or hiding. Because of the focus on objects, our taxonomy can be considered object-oriented; it describes the steganographic operation performed on objects using actions.
In general, patterns can be used to describe the process of hiding information for storage purposes as well as for secretly moving data among two endpoints. To avoid burdening the text, when the “transmissional” nature of the embedding process is not obvious, we will explicitly identify the covert sender and receiving side as to emphasize the origin and the destination of the steganographic communication.
For the specific case of defining the taxonomy as well as to describe patterns, the following formal definitions have been introduced. Please note that in comparison to previous attempts (Figure 1, left side), we heavily simplified our terms and their relations due to the inconsistent pattern namings and terminology aspects
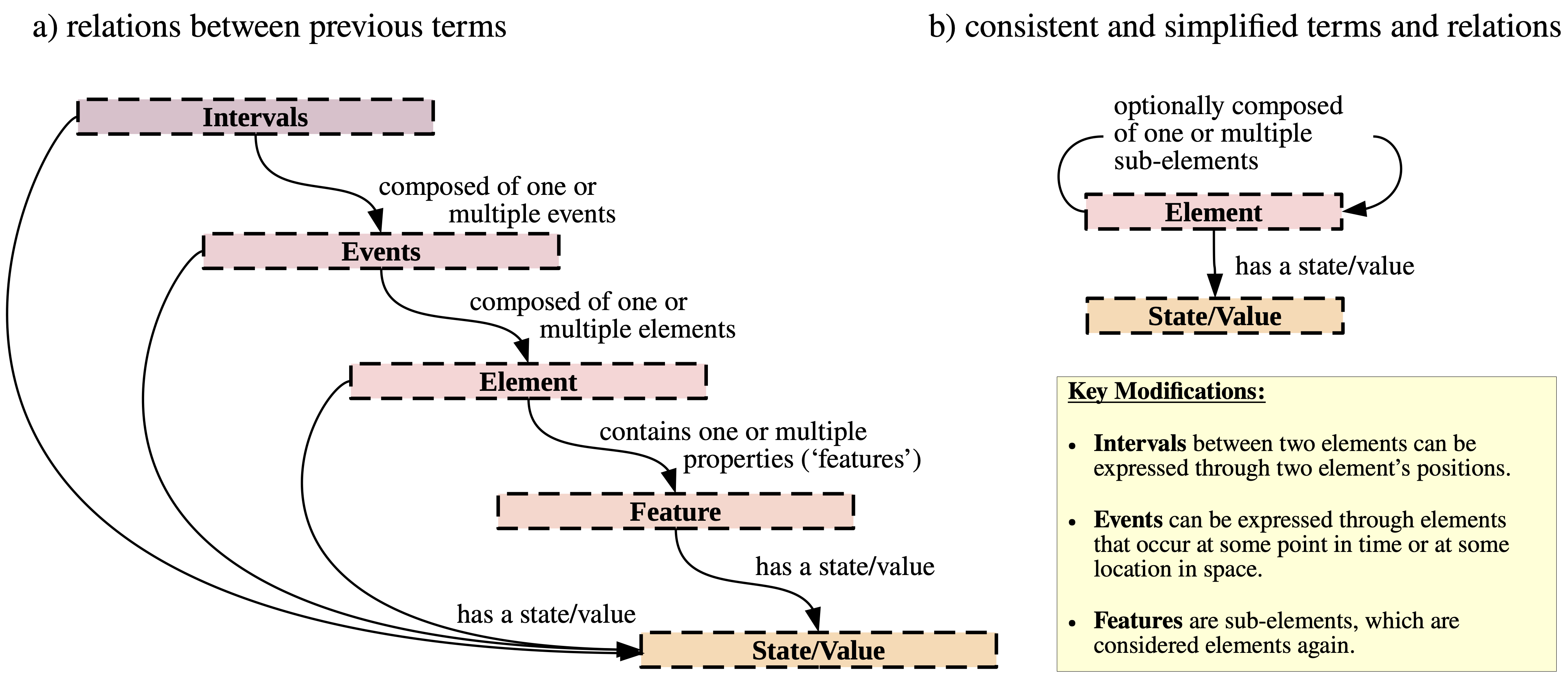 Figure 1: Relations and terms have been simplified between the 2021-taxonomy (a) and the novel taxonomy (b).
Figure 1: Relations and terms have been simplified between the 2021-taxonomy (a) and the novel taxonomy (b).
Modifiable Objects
(see Figure 1, right side and Table 1 for examples):
-
An Element represents the object to be created, modified or deployed for steganographic data hiding. Elements can occur alone or in a sequence, e.g., 1) a network packet; 2) a word/character of a text; 3) a pixel of an image; 4) a CPS command, e.g., a BACnet Read Property command or Who-Is message, a CPS sensor, a CPS sensor’s polling rate, packet sending rate of a flow; 5) a single file, folder or inode.
Sub-elements: Elements can contain further elements, which can be considered their sub-elements (see Figure 2 for an illustration). Sub-elements are equal to elements — the term sub-element just states that some element belongs to a higher-level parent element. Sub-elements can be stored in their parent element or can be a property of that parent element. For instance, an IPv4 network packet can contain option headers which can all be considered elements. Each IPv4 packet and each of its option headers has header fields, which are also elements. Further, each IPv4 packet has a header size, a time at which it occurs, etc., and so does each header field. These properties are also considered elements, although they are virtual, i.e., not explicitly stored in some memory location. Another example could be a CPS sensor as an element that contains several sub-elements, such as a temperature attribute.
-
The State or Value of an element is the actual state or value that an element currently has, i.e., not the property itself, e.g., not the size attribute of a network packet but the actual size value. Examples: 1) the value of a TCP header field (the TCP header element’s actual bit-value) or the IPv4 IHL value; 2) the name of a character’s font 3) the x-, y- or z-coordinate of a player in a 3D game; 4) an actual setpoint of a CPS device; 5) the size value of a single file.
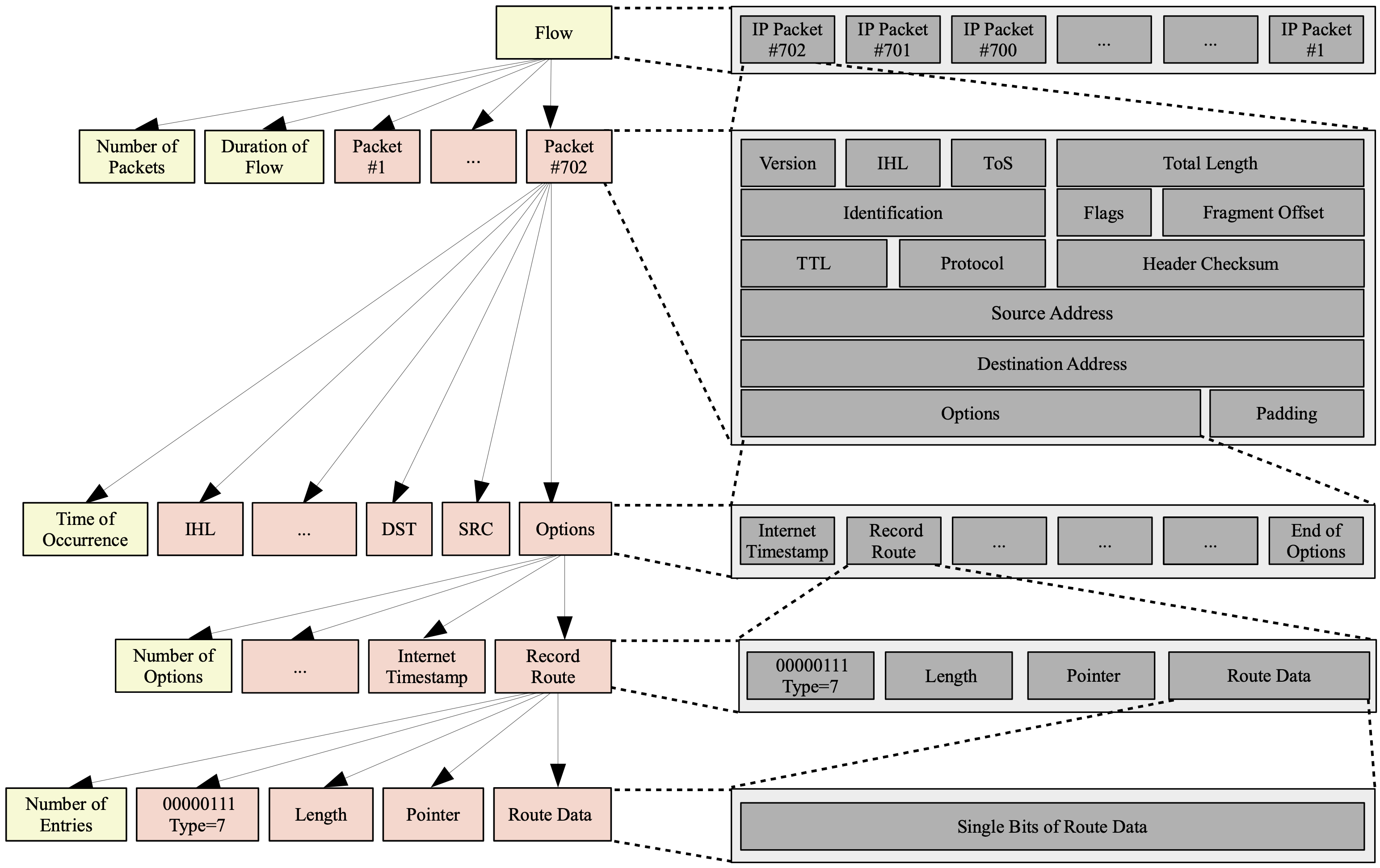 Figure 2: Exemplified illustration of elements and sub-elements for a network flow. The element ‘flow’ contains several sub-elements, including some packets. Each of these packet elements contains further sub-elements, of which the illustrated ‘options’ can be one, containing further sub-elements, and so forth.
Note: Yellow elements are virtual elements, while light-red elements reflect those actually stored inside a parent element.
Figure 2: Exemplified illustration of elements and sub-elements for a network flow. The element ‘flow’ contains several sub-elements, including some packets. Each of these packet elements contains further sub-elements, of which the illustrated ‘options’ can be one, containing further sub-elements, and so forth.
Note: Yellow elements are virtual elements, while light-red elements reflect those actually stored inside a parent element.
Actions
(see Table 1 for examples):
-
The Modulation of an element’s state/value is the selection of one particular state/value out of multiple possible states/values. For instance, if the element is the IPv4 TTL field, its value would have a range between 0 and 255, and modulation would select one of the possible values to embed a secret inside the TTL. Similarly, the state of an element that is a CPS window actuator could switch between open and closed.
General modulation can be applied to various types of states/values, including such that represent reserved/unused or random values. These special cases are represented as sub-patterns in Figure 3.
-
Occurrence is a predominant special case of modulation that appears several times in steganography research and was thus separated from the general modulation above. Occurrence refers to the modulation of the temporal or spatial location: an element, such as an IP packet, can have a sub-element (here in the sense of a property) that describes the time or location of appearance. This appearance element’s value is then modified. For instance, an IP packet occurs at some point in time and a character of text occurs at some location in a text document.
There are two specific variants of Occurrence:
-
Enumeration means that the overall number of occurrences of elements is altered. Enumeration is usually used for a higher-level element (e.g., a network flow) containing lower-level elements (e.g., network packets), e.g., the number of lower-level elements is considered an element (again in the sense of a property) of the higher-level element. For instance, one could have a network flow that contains either 10 or 20 IPv4 packets or a text document that contains 100 or 101 letters to represent a secret information.
-
Positioning selects the temporal/spatial position of one element (optionally in a sequence of elements). Again, the position of an element is an element (property) by itself. For instance, a particular TCP segment could be positioned at some location in a flow to embed a secret.
-
Table 1 : Differentiation between the types of objects used in this paper.
| Domain | Element Examples | State/Value Examples |
| network steganography | network packet (e.g., IP packet); header field (e.g., TCP seq. no.); packet size property; time of occurrence property of a packet | actual packet size in bytes; actual TCP sequence number; time of sending/arrival |
| text steganography | a text; a paragraph; a character; line spacing; font of a character; size of a character; text length | actual color value; actual font name; actual length of text |
| digital media steganography | pixel of an image; PNG file header attributes; color attribute of a pixel; image size property | actual color value; actual image size value |
| cyber-physical systems steganography | a sensor; an actuator; control command (e.g., BACnet ReadProperty); temperature value of a sensor; status of an actuator | actual state of an actuator (open/closed); actual temperature value of a sensor |
| filesystem steganography | file; inode; file creation/deletion timestamp attributes; file size attribute; file header attribute; inode attribute (e.g., inode number field) | file’s actual status (e.g., existent/deleted); actual inode number’s value |
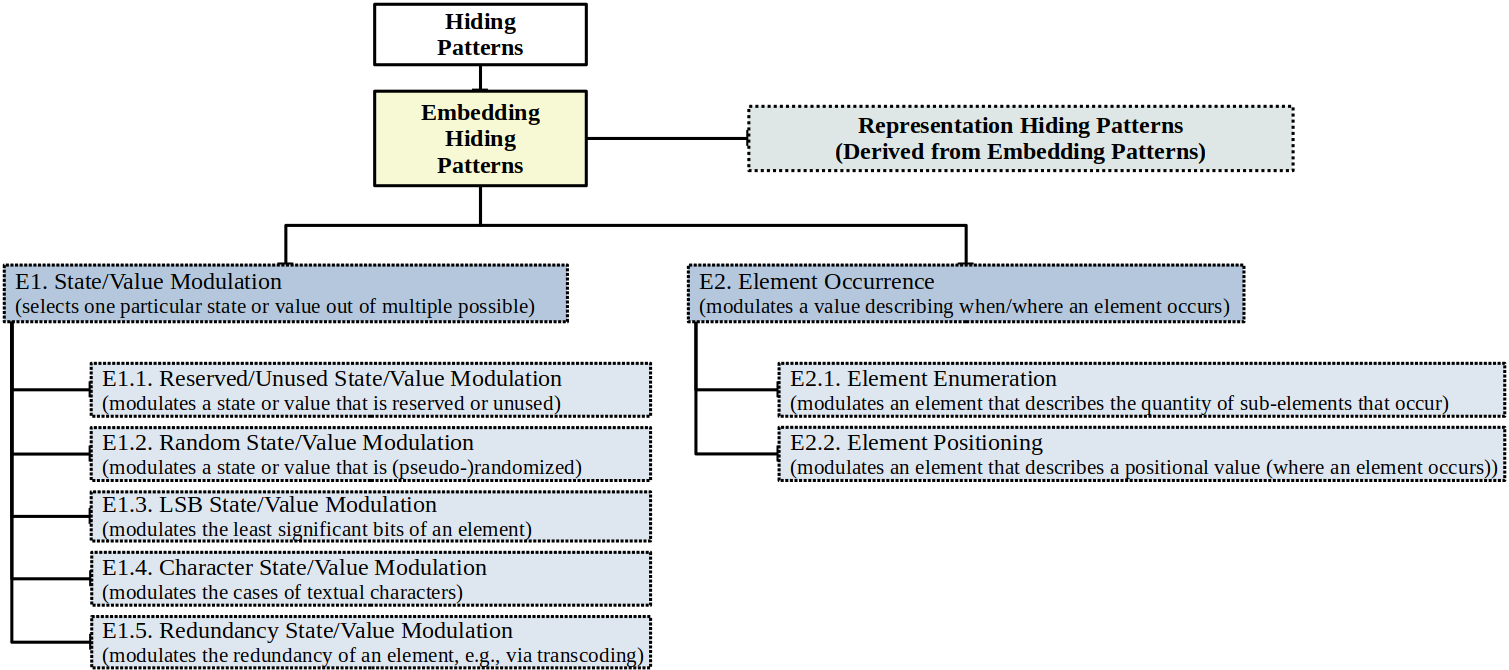 Figure 3: The generic taxonomy’s core component: embedding hiding patterns.
Figure 3: The generic taxonomy’s core component: embedding hiding patterns.